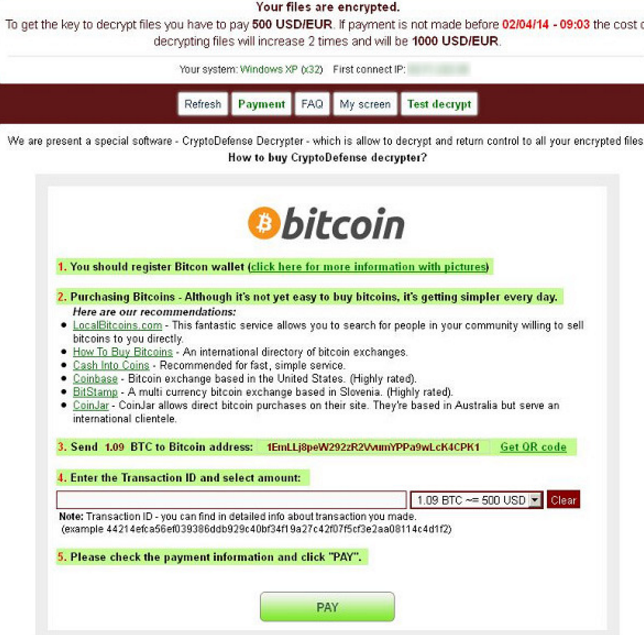
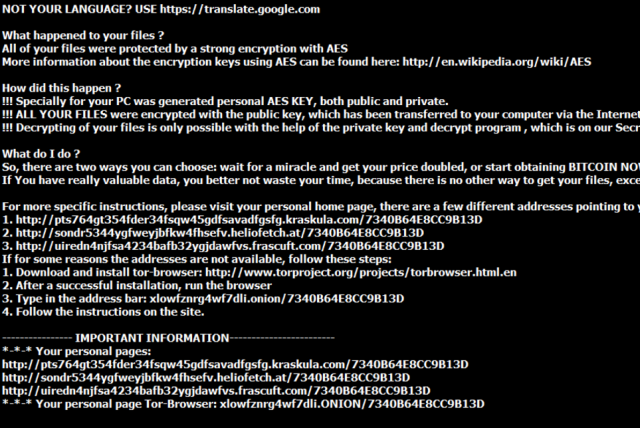
!RecOveR!-fjuqh++.Txt/Png/Htm
Do you know what is !RecOveR!-fjuqh++.Txt/Png/Htm? We classify it as a ransomware. It is easy to find out that your PC is infected with !RecOveR!-fjuqh++.Txt/Png/Htm and the sign is obvious. When your system gets this item inside, all your files will be encrypted at first, and then it will blackmail the users to pay for huge amount of money to rescue these files. That is the main task of ransomware. If you continue to keep it on your PC, such tragedy will occur time by time. Therefore, we advice you to learn more about this malicious stuff and get rid of it with the instruction here.
As mentioned above, !RecOveR!-fjuqh++.Txt/Png/Htm has the power to encode all your files. In general, you will find that the file extension will follow with .ccc, .vvv, .locky, .micro, and so on. When you try to open this files, and it will remind you that your files require decryption key to decode them. Besides, it will leave a readable files for you to solve this dilemma. Without doubt, its purpose is to lead you to follow the instructions on this documents so that it could gain high profits in this way.