TeslaCrypt 3.0 (.micro extension)
TeslaCrypt 3.0 (.micro extension) is considered as a dangerous Ransomware and every PC should avoid it in order to protect their files and data. It has the ability to encrypt every files on the PC and then it will blackmail money from the users. Also, it has the ability to take control over all the data here on your system. In this way, we highly recommend you to eliminate it from your PC, and if you want to know if your PC has been infected, please keep reading this article and judge it from the signs stated here.

As TeslaCrypt 3.0 (.micro extension) is able to affect everything on the PC, it will encrypt the files here. All the formats could be infected, including doc. Xls. Exe. Jpg. Or anything else. And then, when users try to open these files, they will require to provide the encryption key. Obviously, no user will have this item. And then, they will be asked to pay for the key with high charge.
However, the key bought by users will lose effect later and it would not be free forever. TeslaCrypt 3.0 (.micro extension) could do whatever it wants to your files even you agree to pay for the encryption key. Therefore, if you want set your files free and protect your PC, you should remove TeslaCrypt 3.0 (.micro extension) as soon as possible. As you could not easily predict what it has done to your PC, you would not remove all the damages at one time. Here are some guides for your reference.
Effective Steps to Get Rid of TeslaCrypt 3.0 (.micro extension) Virus
Step 1. Uninstall TeslaCrypt 3.0 (.micro extension) related programs and other unwanted software you installed recently.
1. Press “Windows” key and “R” key at the same time to open “Run” window.
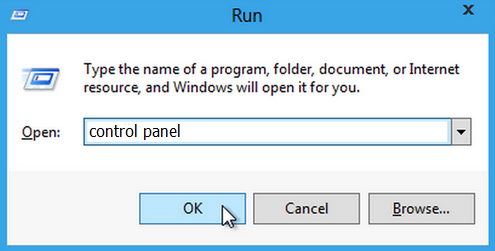
2. As the above image shows, now input “control panel” in the Run window and click OK, then you will see the Control Panel window.
Now select category view, and click on Uninstall a program under the Programs.
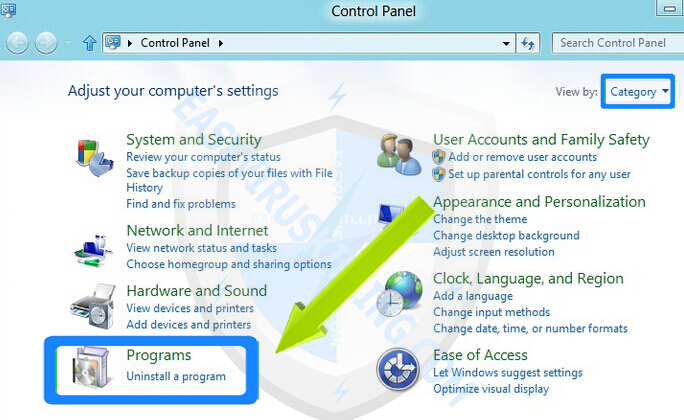
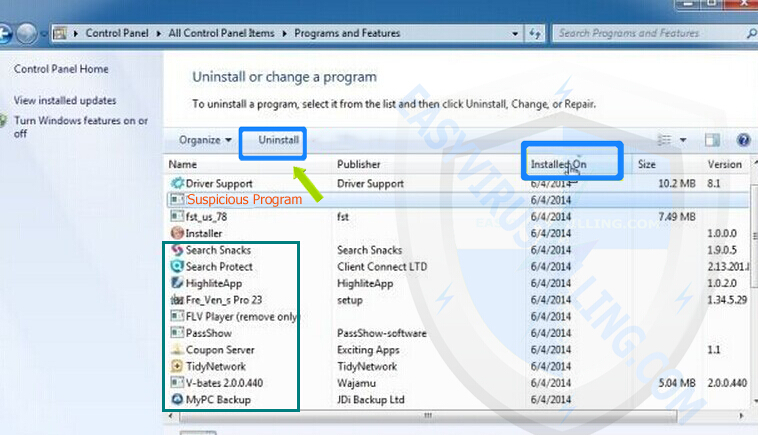
3. Now the Programs and Features window is opened as below.
Please click Installed On to display the latest programs, scroll through the list to find and uninstall TeslaCrypt 3.0 (.micro extension) and other unwanted programs installed recently.
——————————————————————————————————————————-
If you are a Windows 10 user and cannot execute the steps above, please try this method:
1. Click Start Menu on Win 10 screen, and click All apps.
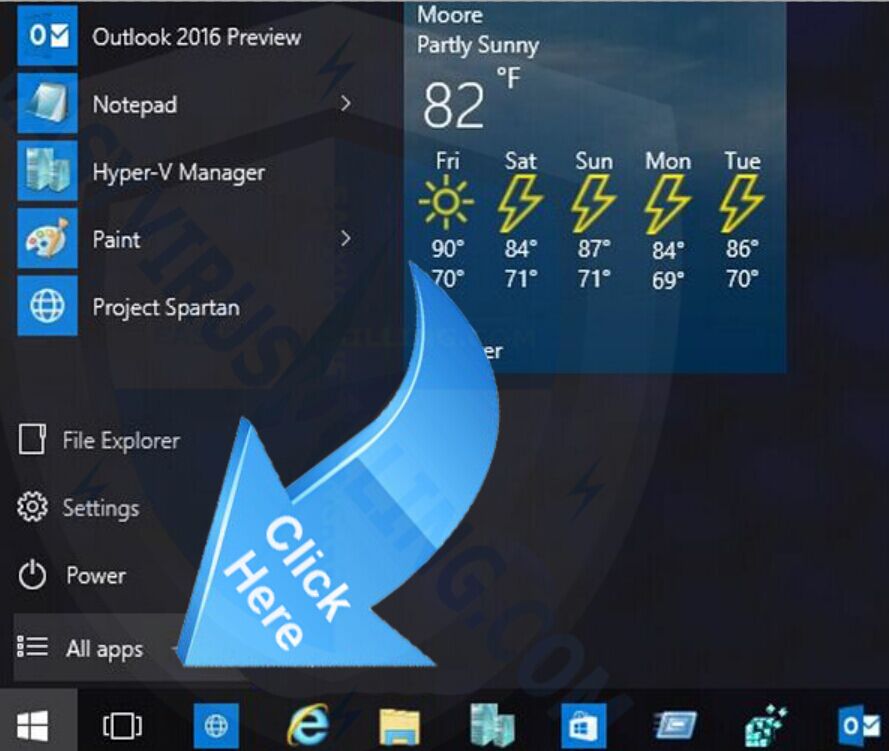
2. Now you can see all apps of your Win 10, find out the unwanted or suspicious program, then right-click it and select Uninstall.
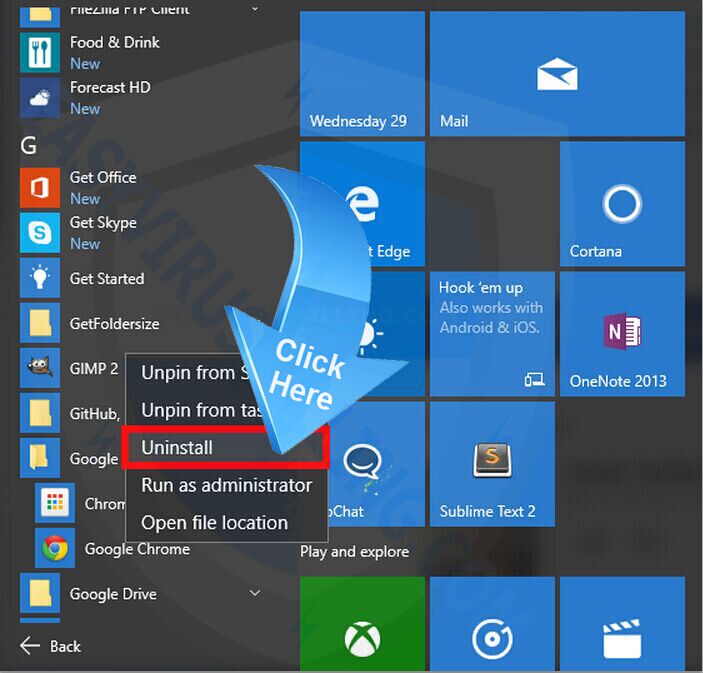
(Note: Please go to next step if you do not find any suspicious program in the list)
Step 2. Remove Microsoft Edge/ Internet Explorer add-on, Chrome extension and Firefox add-on related with TeslaCrypt 3.0 (.micro extension).
Microsoft Edge User
(Since Edge browser does not have extensions function now, what you need is just to reset homepage and search engine.)
1. Set your homepage page on Microsoft Edge to remove hijacker virus.
- Select More (…) on the address bar, then Settings
- Under Open with, select A specific page or pages
- select Custom to enter the URL of page you want to set as homepage
———————————————————————————————————————————————-
2 . Set your default search engine to remove search redirect virus.
- Select More (…) on the address bar, then Settings
- Click View advanced settings
- Click <Add new> under “Search in the address bar with”, then input the search engine you like
- Now select the search engine you like and click Add as default
Google Chrome User
- Click the Chrome menu
 on the browser toolbar.
on the browser toolbar. - Click Tools.
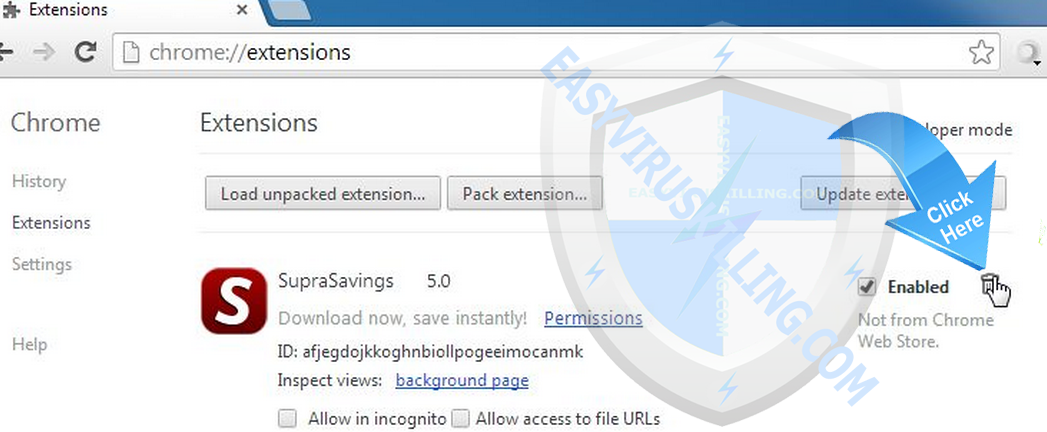
- Select Extensions.
- Click the trash can icon
 to delete TeslaCrypt 3.0 (.micro extension) extension.
to delete TeslaCrypt 3.0 (.micro extension) extension. - Make sure to remove all extensions you do not know or need.
- A confirmation dialog appears, click Remove.
Firefox User
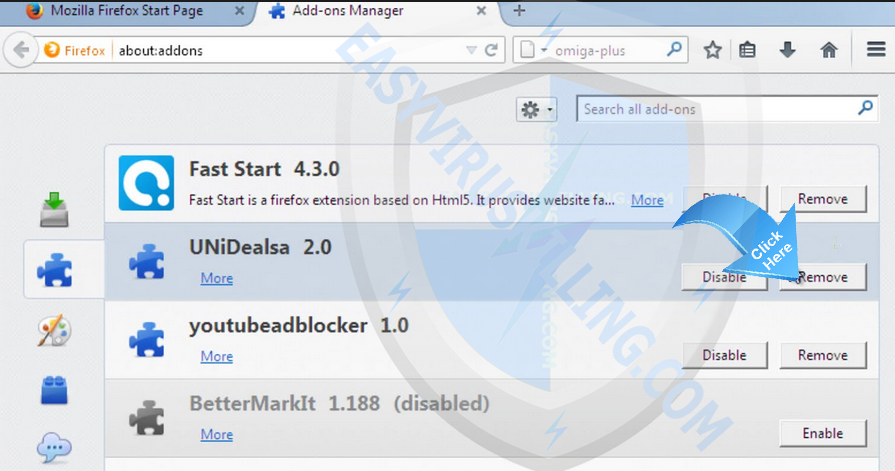
- Click the menu button

 and choose Add-ons. The Add-ons Manager tab will open.
and choose Add-ons. The Add-ons Manager tab will open. - In the Add-ons Manager tab, select the Extensions panel.
- Make sure to remove all extensions you do not know or need.
- Click Disable or Remove button of TeslaCrypt 3.0 (.micro extension).
- Click Restart now if it pops up.
Internet Explorer User
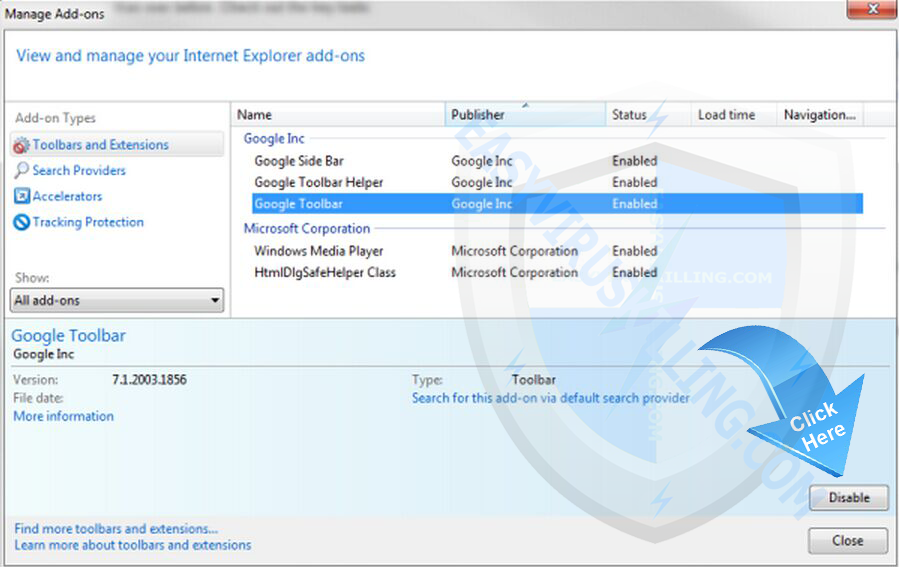
- Open the IE, click the Tools button

, and then click Manage add-ons.
- Click Toolbars and Extensions on left side of the window., and then select TeslaCrypt 3.0 (.micro extension)
- Make sure to remove all BHO’s you do not know or need.
- If the add-on can be deleted, you’ll see the Remove option. Click Remove and then click Close. Otherwise click Disable button.
Step 3. Diagnose your computer with SpyHunter and remove TeslaCrypt 3.0 (.micro extension) and other viruses (Important Step)
SpyHunter is best of the best AntiSpyware/ AntiMalware tool capable of detecting and removing all the Adware, Spyware, Malware, PUP, and Trojan Horse hiding in Windows computer. Start a free scan with SpyHunter now and find out all malicious files related with TeslaCrypt 3.0 (.micro extension) virus.
1. Click this link: “Download SpyHunter” or the blue button below to download SpyHunter safety:
Tips: After SpyHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning ” This type of file can harm your computer. Do you want to keep Download_Spyhunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
(Notes – If you do not need it any more, please follow instructions on SpyHunter uninstall. SpyHunter`s free version provides unlimited free scans and detection. After it detects malicious files, processes and registry entries, you can follow the scan results to manually locate and remove them on your own; or to purchase its full version to automatically remove the virus with ease. Meanwhile, the full version of SpyHunter will offers you unlimited one-on-one professional help for any malware related issue by its official PC expert.)
2. Once downloaded, please double-click SpyHunter-Installer.exe to start the installation of SpyHunter.
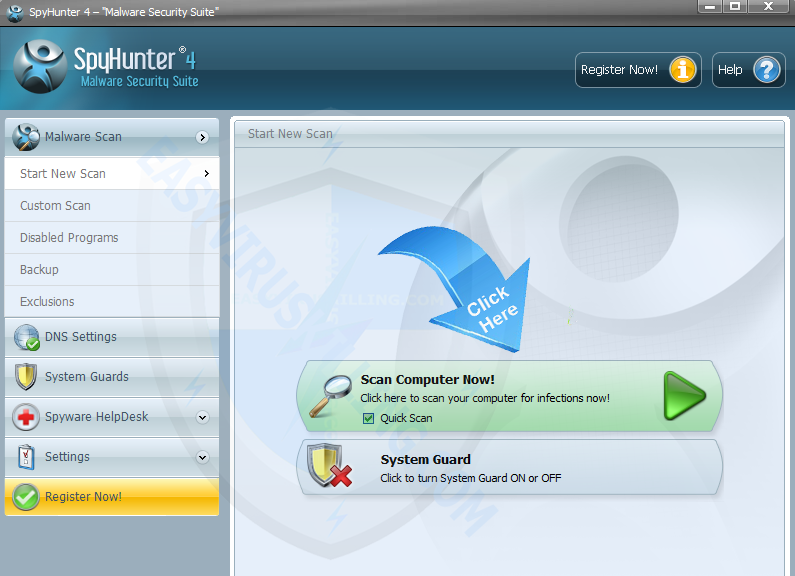
3. When SpyHunter is installed, it will be run automatically, then click Scan Computer Now to detect TeslaCrypt 3.0 (.micro extension) related threats:
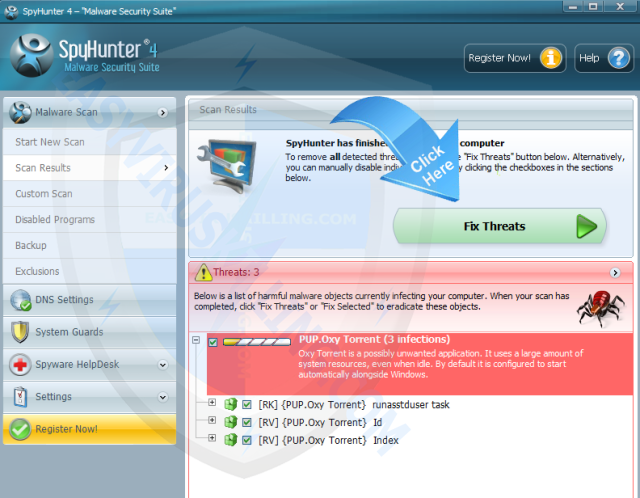
4. Once SpyHunter completes the scan, please click Fix Threats to get rid of TeslaCrypt 3.0 (.micro extension).
Step 4. Use RegHunter to fix all damaged registry errors and security bugs caused by TeslaCrypt 3.0 (.micro extension).
Notes: If TeslaCrypt 3.0 (.micro extension) virus still appear after you removed it with SpyHunter, it is clear that there are some registry errors and security bugs needed to be fixed. TeslaCrypt 3.0 (.micro extension) virus can be re-activated by malicious codes it injected into your Registry, therefore we need to fix those registry errors and security codes and recover the healthy system files. After we fix the Registry, TeslaCrypt 3.0 (.micro extension) will not have any chance to re-activate itself again. When we do any operation related with Registry, we need to be 100% careful, because any small mistake we make in the Registry can lead to severe problems, therefore, we recommend every user to let RegHunter help you complete the complicated operations in Registry automatically. It is one of the best tool which can maximize system performance and fix registry and system errors. Run it now:
1. Click this link: “Download RegHunter” or the blue green below to download RegHunter safety:
Tips: After RegHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning “This type of file can harm your computer. Do you want to keep Download_Reghunter-Installer.exe anyway?“, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
Notes – If you do not need it any more, please follow instructions on RegHunter uninstall. RegHunter`s free version provides unlimited free scans and detection. After it detects corrupted registry files and system errors files, you can follow the scan results to manually replace them with healthy files copied from healthy PC on your own; or to purchase its full version to automatically fix the Registry and errors with ease. Meanwhile, the full version of RegHunter will offers you great features to optimize your system performance.)
2. Once downloaded, then double-click RegHunter-Installer.exe to start the installation of RegHunter.
3. When RegHunter is installed, it will be run automatically, then click Scan for Registry Errors Now! to detect files corrupted by TeslaCrypt 3.0 (.micro extension):

4. Once RegHunter completes the scan, please click Repair All Errors to solve security bugs related with TeslaCrypt 3.0 (.micro extension).
Step 5. Restore or Recover Damaged Files
To PC Users with Healthy Backup Files
If you have backup your personal files or documents before the invading of TeslaCrypt 3.0 (.micro extension), now you can delete all the encrypted files on your PC, and then copy the backup files from your external devices or download them from your Cloud account. You can open these healthy files at ease now since the codes of ransomware have been removed and they cannot encrypt your files again.
To PC Users without Backup Files
If you do not have any backup of your personal files, or if your backup files have been damaged as well, you need to use professional data recovery software to recover your files. After reviewing lots of data recovery software, our tech team picked out the best data recovery software in the industry: Stellar Data Recovery, Data Recovery Pro and Kernel Data Recovery. To get your important files back, It’s worthy to try such top-class data recovery software.
Option One – Stellar Data Recovery
Stellar Phoenix Windows Data Recovery is your best disaster recovery solution to get back all your lost and deleted files, photos, music and videos after all event of data loss like accidental deletion, disk corruption, or storage media formatting etc. This risk-free application supports recovering data from all types of Windows hard drives, USB drives, memory cards, digital cameras, and mobile phones. The tool has a knack of scanning 2TB or more of storage space in a single operation, thus providing you with a more robust solution for performing complex data recovery too. Follow the steps here to install Stellar Phoenix Windows Data Recovery quickly:
1. Click the button below to open download Stellar Phoenix Windows Data Recovery , and Double-click installation file “Stellar_WinDataRecovery_Home “ to install it:

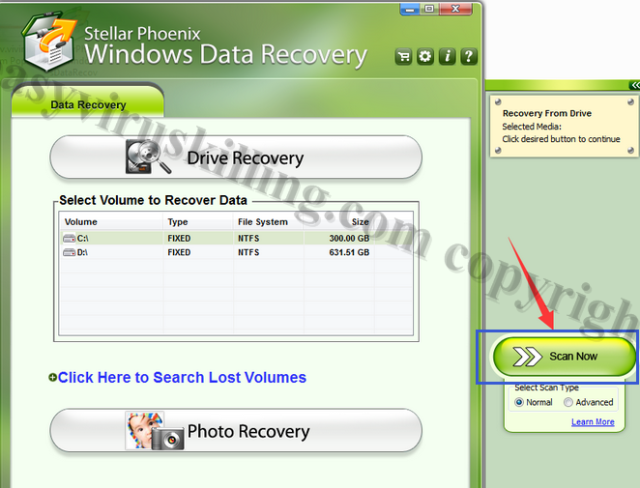
2. Once installed, click Scan Now button to detect the corrupted files in your system:
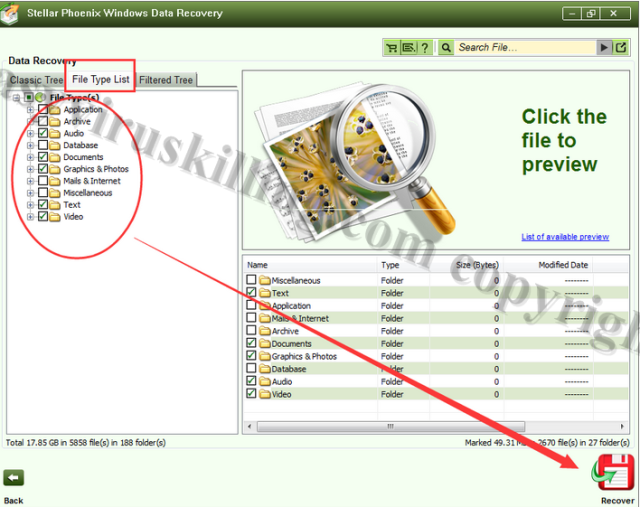
3. Once it complete the scan, please select the file types you want to recover and then click Recover button:
Option Two – Data Recovery Pro
Since Ransomware such as TeslaCrypt 3.0 (.micro extension) uses the most advanced codes to encrypt your files, it is necessary to try different Data Recovery Software to decrypt different types of codes written by hacker. After you tried the Stella software, most of your files may still be encrypted, please do not give up, now download Data Recovery Pro to rescue your files again. It is one of the best data recovery tool and it so powerful it can recover a wide variety of file types, including recycled, compressed and encrypted. Download it now and let it at least rescue some of your important files:
1. Click this link “Data Recovery Pro Download ” or the button below to download and install Data Recovery Pro:
2. Once installed, select Quick Scan or Full Scan and then click “Start Scan“to detect files damages by TeslaCrypt 3.0 (.micro extension):
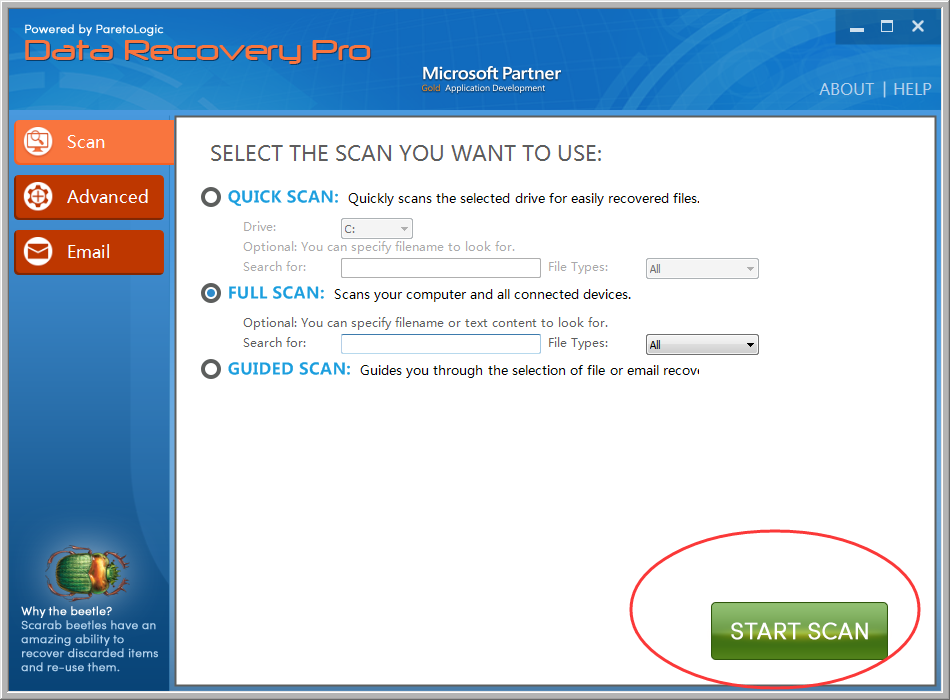
3. Once the scan completes, check all the files type you want to recover and then click “RECOVER” button to rescue your files from TeslaCrypt 3.0 (.micro extension).
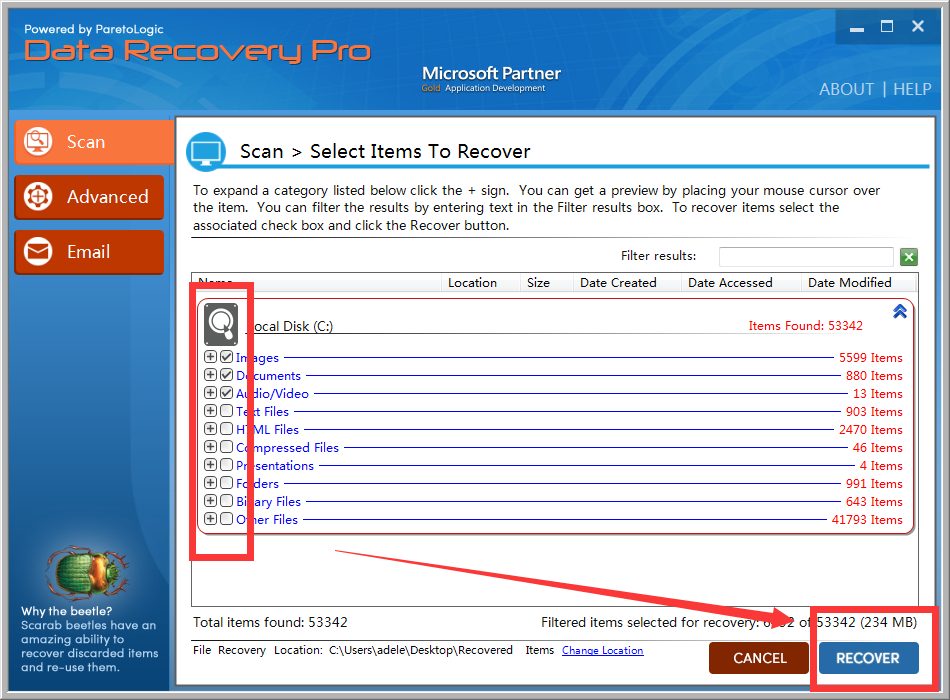
Option Three – Kernel Data Recovery
If you the first two software cannot help you restore your files, you can also try another great data recovery software – Kernel. Here are 6 recover tools from Kernel for recovering diffident files, click the links below to get the recovery tool you need:
Micosoft Office Word Files Recovery
Micosoft Office Excel Files Recovery
Micosoft Office Access Files Recovery
Micosoft Office PowerPoint Files Recovery
Notes: As we all know, TeslaCrypt 3.0 (.micro extension) is the most dangerous ransomware made by top hacker, and it is extremely difficult to recover all the files encrypted by TeslaCrypt 3.0 (.micro extension). The above data recovery tools may not be effective on all the infected PCs, some users used them to restore parts or all of their files, and some others could not recover any file. Therefore we can not 100% promise these tools will work for you, we just recommend them to you as reference. We hope that you will be the lucky one who can get your precious files back. Good luck with you.
Tips
TeslaCrypt 3.0 (.micro extension) virus is mainly spread online through resources such as Free Software, Spam Email and Porn Websites. To avoid virus and malware like TeslaCrypt 3.0 (.micro extension) infect your computer again, you should keep these tips in your mind:
1. Always select Advance or Custom Install if you want to install any free software;
2. Scan all attached files of emails you receive, even the emails sent from Contacts;
3. It’s best not to visit porn websites, which are often hosted by cyber criminal and they may harm your system severely.






