About [email protected]
[email protected] is an extremely destructive virus you will never want to see on your system, because it is designed by hacker and applied to encrypt computer users’ personal files! Similar to notorious ransomware such as CryptoWall, FUCKEDFILES, and HELP_DECRYPT, [email protected] virus will execute command prompt to inject codes on your personal files make them unusable. Lots of your Microsoft Office files, images / pics, audio files, video files, PDF files and any kind of files cannot be opened normally and all their names have been changed into something with a weird extension like [email protected] or .VVV.
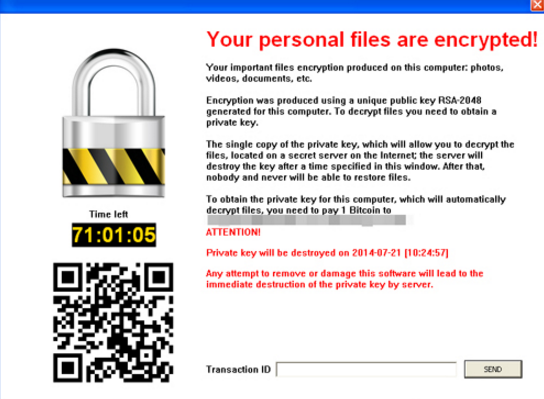
This is common form of online crime that hackers use to make money, by encrypting your files, [email protected] virus forces you to contact the virus maker and pay lots of money to recover your precious personal files. Your computer can be hacked by [email protected] ransomware when you open attachments of spam emails, visit adult websites, download freeware or torrent files from unknown file-sharing websites, or update installed apps from third party websites. If it invades your system, other forms of threats will also be downloaded from remote server to cause more severe system problems. To avoid more of files being locked by [email protected] ransomware, and get your healthy PC back, you need to get rid of [email protected] virus immediately. Ransomware removing is a tough task, so our tech team works out a [email protected] removal guide for you as reference, we sincerely hope that the removal steps below can assist you to delete the malware completely.
Steps for Removing [email protected] and Recovering Files
This tutorial contains two Parts. Part One will guide you to get rid of codes of [email protected] virus and repair registry errors, which can avoid more of your files being encrypted by the ransomware. In Part Two, we will guide you to recover some damaged files.
Part One – Get Rid of [email protected] Virus Manually or Automatically
Manual Removal Steps (Complicated Method Applies to Advanced PC Users)
Step 1. Show all hidden files to find out malicious files of [email protected]
Step 2. Search and remove harmful files related with [email protected]
Step 3. Search and delete [email protected] related registry files
Automatic Removal Steps (Easy Method Applies to All PC Users)
Step 1. Run SpyHunter to detect and remove malicious codes of [email protected] infection.
Step 2. Run RegHunter to fix registry files and security bugs caused by [email protected].
Part Two – Restore or Recover Damaged Files
- Restore all your files from your Back-up;
- Repair damaged files with data recovery software.
Part One – Get Rid of [email protected] Virus Manually or Automatically
Manual Removal Steps
Step 1. Show all hidden files to find out malicious files of [email protected]
On Windows 7 / Vista Computer
- Right-click the Windows Logo button and choose Open Windows Explorer.
- Click Organize and choose Folder and Search Options.
- Click the View tab, select Show hidden files and folders and then clear the checkbox for Hide protected system operating files.
- Click Yes on the warning and then click OK.
On Windows 8 Computer
- On your keyboard press the Windows + E keys.
- Click the View tab.
- Check File name extensions and Hidden items
Step 2. Search and remove harmful files related with [email protected]
(The files on your computer may appear with different name, if cannot find out the files listed below, you should use the auto steps)
%Temp%\[random name]
%AppData%\[virus name]
%LocalAppData%\[virus name]
%CommonAppData%\[malware name]
%AllUsersProfile%random.exe
Step 3. Search and delete [email protected] related registry files:
1. Open Registry Editor first:
On Windows 7 / Vista Computer
- Click Start button
- Select Run button
- Type: regedit
- Click OK button
On Windows 8 Computer
- Press Win [Windows key] + R on your keyboard. This can be done either while at Windows 8 Start menu/Metro screen or on Windows 8 desktop
- At the dialog box that pops open, type regedit.exe and hit OK
- Once you hit OK, Windows UAC will prompt you to confirm you want to open Register Editor — hit “Yes”
2. Find out and remove all harmful registry files related with [email protected] virus listed below:
(The registry files on your computer may appear with different name, if cannot find out the files listed below, you should use auto steps.)
HKEY_LOCAL_MACHINESOFTWAREsupWPM
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesWpm
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain “Default_Page_URL”
HKEY_LOCAL_Machine\Software\Classes\[malware name]
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\[malware name]
Automatic Removal Steps
Manual removal needs advanced PC skills, if you do not have enough skills and experience to find out [email protected] files accurately, you may ruin your system for removing important system files. Therefore, if you are not a user with Advanced tech skills, it’s best to use these Auto Steps to solve your problem easily and safely:
Step 1. Run SpyHunter to detect and remove malicious codes of [email protected] infection.
1. Click the blue button below to open of SpyHunter.
Tips: After SpyHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning ” This type of file can harm your computer. Do you want to keep Download_Spyhunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
(Notes – If you do not need it any more, please follow instructions on SpyHunter uninstall. SpyHunter`s free version provides unlimited free scans and detection. After it detects malicious files, processes and registry entries, you can follow the scan results to manually locate and remove them on your own; or to purchase its full version to automatically remove the virus with ease. Meanwhile, the full version of SpyHunter will offers you unlimited one-on-one professional help for any malware related issue by its official PC expert.)
2. On the SpyHunter page, please click Download Free Scanner to download SpyHunter safely and quickly.
Tips: After SpyHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning ” This type of file can harm your computer. Do you want to keep Download_Spyhunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, please double-click SpyHunter-Installer.exe to start the installation of SpyHunter.
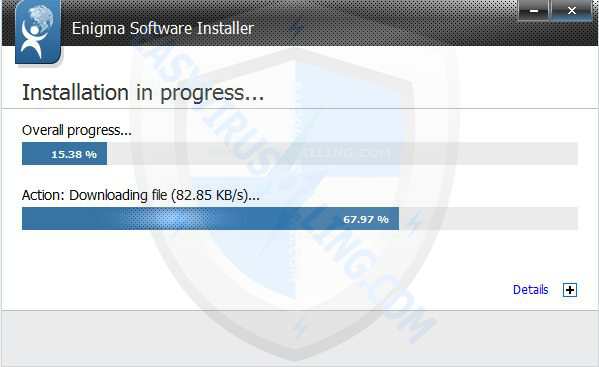
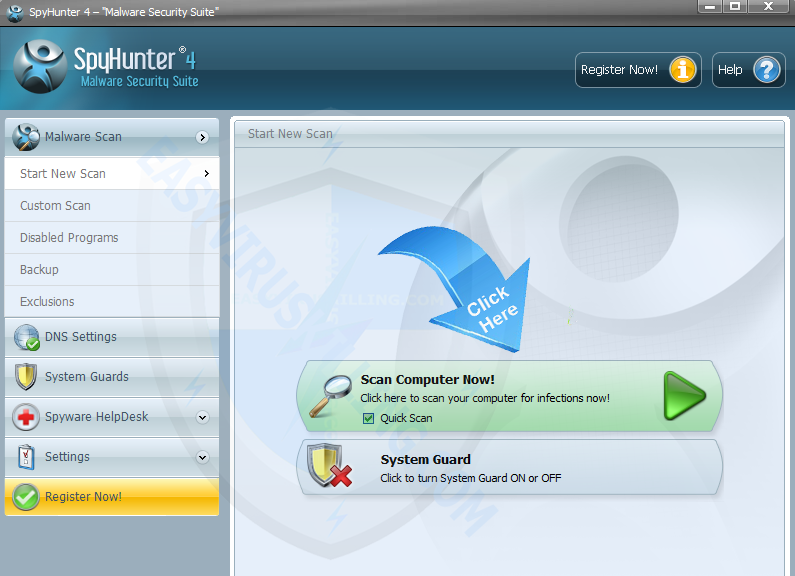
4. When SpyHunter is installed, it will be run automatically, then click Scan Computer Now to detect [email protected] related threats:
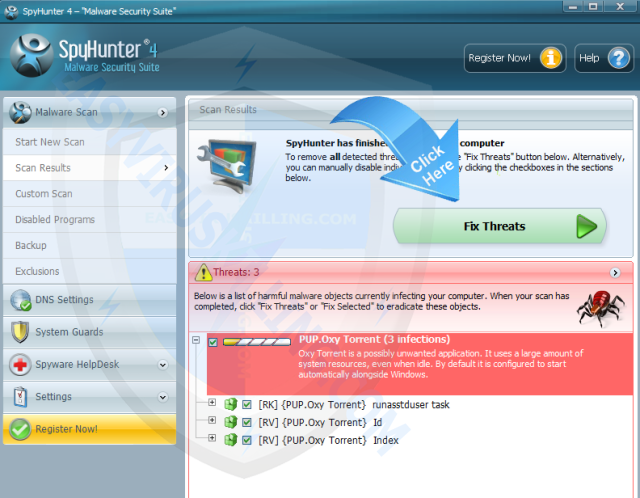
5. Once SpyHunter completes the scan, please click Fix Threats to get rid of [email protected].
Step 2. Run RegHunter to fix registry files and security bugs caused by [email protected].
1. Click the green button below to open of RegHunter:
Tips: After RegHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning “This type of file can harm your computer. Do you want to keep Download_Reghunter-Installer.exe anyway?“, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
Notes – If you do not need it any more, please follow instructions on RegHunter uninstall. RegHunter`s free version provides unlimited free scans and detection. After it detects corrupted registry files and system errors files, you can follow the scan results to manually replace them with healthy files copied from healthy PC on your own; or to purchase its full version to automatically fix the Registry and errors with ease. Meanwhile, the full version of RegHunter will offers you great features to optimize your system performance.)
2. On the RegHunter page, please click Free PC Diagnosis to download RegHunter safely and quickly.
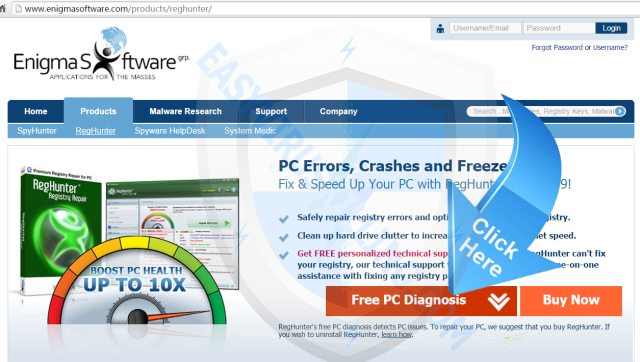
Tips: After RegHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning “This type of file can harm your computer. Do you want to keep Download_Reghunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, then double-click RegHunter-Installer.exe to start the installation of RegHunter.
4. When RegHunter is installed, it will be run automatically, then click Scan for Registry Errors Now! to detect files corrupted by [email protected]:

5. Once RegHunter completes the scan, please click Repair All Errors to solve security bugs related with [email protected].
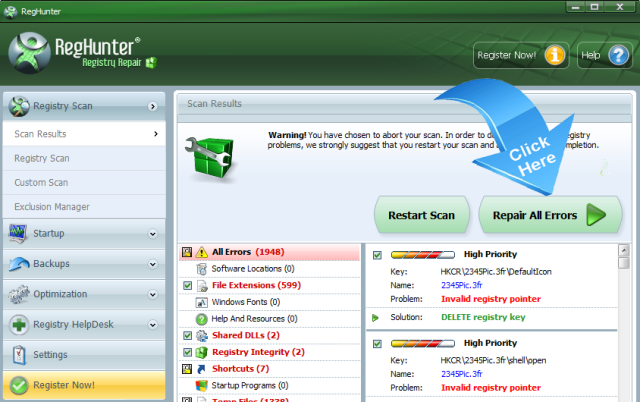
With the manual and automatic removal steps above, the codes and executive files of [email protected] can be removed completely, that means this ransomware cannot encrypt more files of your PC. However, removal of [email protected] virus does not mean that you can open your infected files normally. All the encrypted files corrupted by [email protected] are still inaccessible, if you want get your files back, your need to complete steps in Part Two.
Part Two – Restore or Recover Damaged Files
To PC Users with Healthy Backup Files
If you have backup your personal files or documents before the invading of [email protected], now you can delete all the encrypted files on your PC, and then copy the backup files from your external devices or download them from your Cloud account. You can open these healthy files at ease now since the codes of ransomware have been removed and they cannot encrypt your files again.
To PC Users without Backup Files
If you do not have any backup of your personal files, or if your backup files have been damaged as well, you need to use professional data recovery software to recover your files. After reviewing lots of data recovery software, our tech team picked out the best data recovery software in the industry: Stellar Data Recovery and Kernel Data Recovery. To get your important files back, It’s worthy to try such top-class data recovery software.
Option One – Stellar Data Recovery
Stellar Phoenix Windows Data Recovery is your best disaster recovery solution to get back all your lost and deleted files, photos, music and videos after all event of data loss like accidental deletion, disk corruption, or storage media formatting etc. This risk-free application supports recovering data from all types of Windows hard drives, USB drives, memory cards, digital cameras, and mobile phones. The tool has a knack of scanning 2TB or more of storage space in a single operation, thus providing you with a more robust solution for performing complex data recovery too. Follow the steps here to install Stellar Phoenix Windows Data Recovery quickly:
1. Click the button below to open download page of Stellar Phoenix Windows Data Recovery:

2. Click Free Download button to get the installation file “StellarPhoenixWindowsDataRecovery-Home.exe” and double-click it to install it:
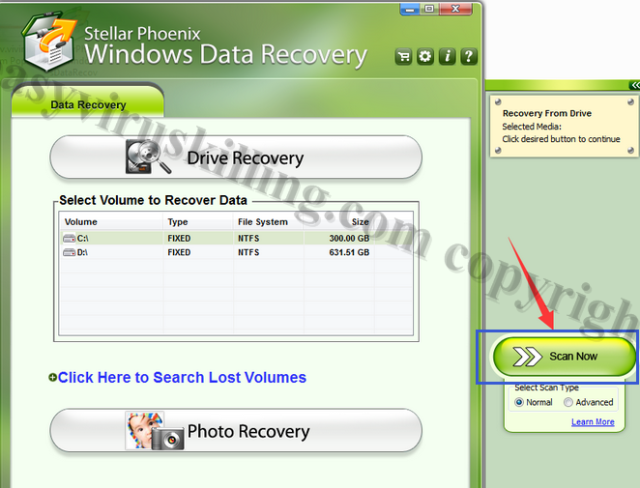
3. Once installed, click Scan Now button to detect the corrupted files in your system:
4. Once it complete the scan, please select the file types you want to recover and then click Recover button:
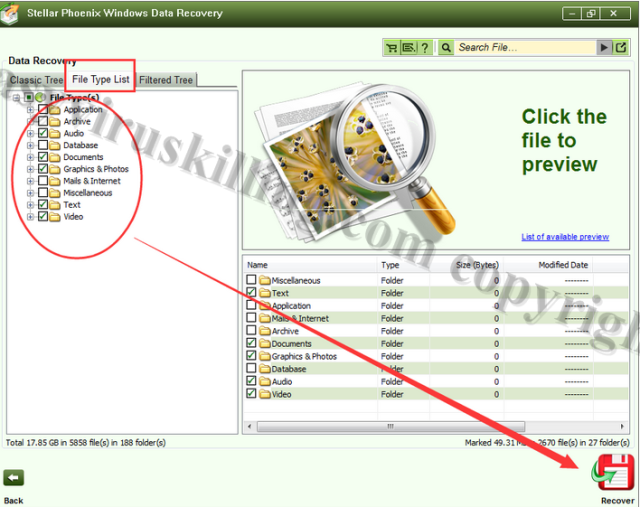
Note: To execute the data recovery, you need to register the full version of Stellar software.
Option Two – Kernel Data Recovery
If you Stella cannot help you restore your files, you can also try another great data recovery software – Kernel. Here are 6 recover tools from Kernel for recovering diffident files, click the links below to get the recovery tool you need:
Micosoft Office Word Files Recovery
Micosoft Office Excel Files Recovery
Micosoft Office Access Files Recovery
Micosoft Office PowerPoint Files Recovery
Notes: As we all know, [email protected] is the most dangerous ransomware made by top hacker, and it is extremely difficult to recover all the files encrypted by [email protected]. The above Kernel tools may not be effective on all the infected PCs, some users used them to restore parts or all of their files, and some others could not recover any file. Therefore we can not 100% promise these tools will work for you, we just recommend them to you as reference. We hope that you will be the lucky one who can get your precious files back. Good luck with you.





