What tphwabi Extension Ransomware Causes?
tphwabi Extension virus is mainly activated by codes attached on spam emails. In case you open the ZIP attachment from a fake or spam email disguises as normal email from your Contacts, tphwabi Extension ransomware immediately invades your computer and encrypt your files within a few seconds, then you will be severe situation as other victims experienced:
Please help me, a severe virus encrypted 12000 files with tphwabi Extension.I followed the instruction removed it, ran a full scan and made sure it’s TRULY gone, but it left a horrible ordeal this virus has Renamed 12327 files in my computer and added (appended) a random name like tphwabi Extension.to all those files including txt files, pdf files, and graphical files some of them were systemic files it has malfunctioned almost all programs in my computer.when I rename them, they’re not the same they’re whether corrupted or if a txt file they’re a bunch of codes
How to Decrypt files that are encrypted with tphwabi Extension?I have ran every maleware and virus checker I can think of and they have found nothing of the dirty ransomware. But there are files that are still encrypted that I can’t replace from doc, pix, to pdf files can some one help.
Just a few days ago our WD mybook live was hacked and im unable to open word documents or some images due to extension. tphwabi extension at the end of these documents.
Tphwabi Extension ransomware damages your programs by running lots of dangerous and unstoppable tasks in the background. It uses codes to infects all your file s(images, music, videos, docs, txts, etc). What it wants is to force you pay ransom money to a account and it claims that after you pay you can get your files back. So far, there are millions of PC users got infected by such tphwabi Extension ransomware and help decrypt virus, and almost all of them cannot recovery their files. As we know, all personal files are important to everyone, thus the hack design this virus to steal users money. And the hack experts, lots of victims compromise and finally send the ransom money. But from research, we find that it is hard to restore those files even though users pay ransom money, it is a trap set by cyber criminals. You should never pay money to the hacker, or they may hack your banking account as well. Follow the steps below to get rid of the tphwabi Extension ransomware completely and prevent more files being infected.
Steps for Removing tphwabi Extension Virus
Manual Steps (Experienced and skilled computer users can use this advanced Manual Removal method )
Step One. Display all hidden files via altering folder settings
Step Two. Find and remove all suspicious files associated with tphwabi Extension
Step Three. Find and delete all harmful registry files generated by tphwabi Extension
Step Four. Uninstall all Potentially Unwanted Programs related with tphwabi Extension
Step Five. Delete unwanted and unknown IE plug-in, Firefox add-on and Chrome extensions related with tphwabi Extension
Automatic Steps (Good and easy for most of PC users to delete tphwabi Extension )
Step One. Install SpyHunter to remove tphwabi Extension virus and other hidden threats.
Step Two. Install RegHunter to fix all damaged registry files and make up the security exploits.
Step Three. Reset Chrome, Firefox and IE to clean up all malicious codes and cookies of tphwabi Extension.
Manual Steps (Experienced and skilled computer users can use this advanced Manual Removal method )
Step One. Display all hidden files via altering folder settings
Windows 7 / Vista User
- Right-click the Windows Logo button and choose Open Windows Explorer.
- Click Organize and choose Folder and Search Options.
- Click the View tab, select Show hidden files and folders and then clear the checkbox for Hide protected system operating files.
- Click Yes on the warning and then click OK.
Windows 8 User
- On your keyboard press the Windows + E keys.
- Click the View tab.
- Check File name extensions and Hidden items
Step Two. Find and remove all suspicious files associated with tphwabi Extension
(You may not be able to find out all files listed below as the virus keeps changing its files with name and path.)
%Temp%\[adware name]
%CommonAppData%\[adware name]
%AllUsersProfile%random.exe
%LocalAppData%\[adware name].exe
Step Three. Find and delete all harmful registry files generated by tphwabi Extension
1. Open Registry Editor first:
Windows 7 / Vista User
- Click Start button
- Select Run button
- Type: regedit
- Click OK button
Windows 8 User
- Press Win [Windows key] + R on your keyboard. This can be done either while at Windows 8 Start menu/Metro screen or on Windows 8 desktop
- At the dialog box that pops open, type regedit.exe and hit OK
- Once you hit OK, Windows UAC will prompt you to confirm you want to open Register Editor — hit “Yes”
2. Find out and remove all harmful registry files related with tphwabi Extension virus listed below:
(You may not be able to find out all files listed below as the virus keeps changing its files with name and path.)
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun
HKEY_LOCAL_Machine\Software\Classes\[adware name]
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain “Default_Page_URL”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\[adware name]
Step Four. Uninstall all Potentially Unwanted Programs related with tphwabi Extension
On Windows 7 / Vista Computer
1. Click on the Start button to open your Start Menu, then Click Control Panel
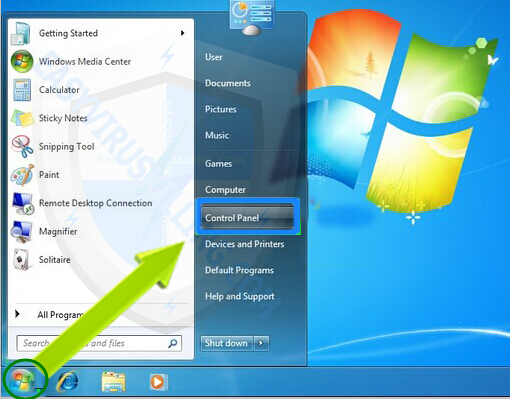
2. In Control Panel, click on Uninstall a program under the Programs category
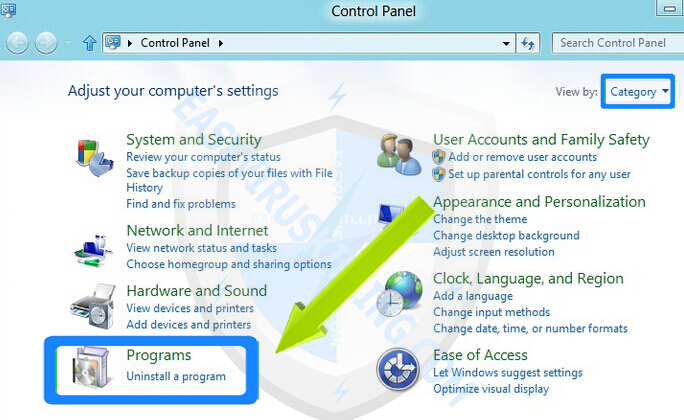
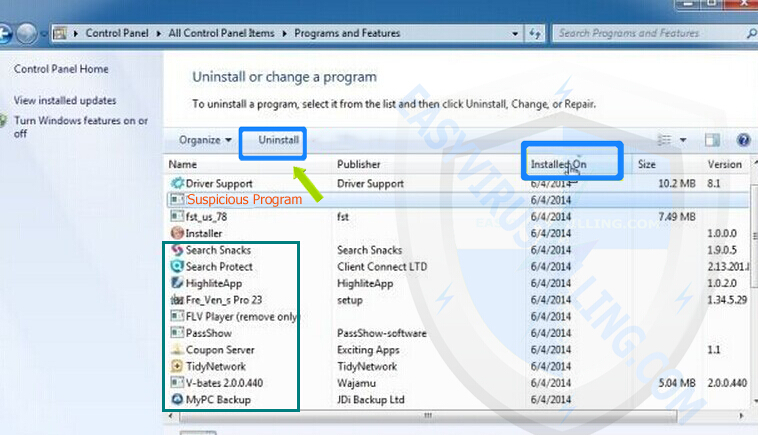
3. In the Programs and Features window, click Installed On to display the latest programs, scroll through the list to seek and uninstall Tphwabi Extension and other unwanted and unfamiliar programs that look suspicious.
On Windows 8 Computer
1. Open the Settings Charm Bar by pressing Windows key  + I key on your keyboard at the same time, then click on the Control Panel option
+ I key on your keyboard at the same time, then click on the Control Panel option
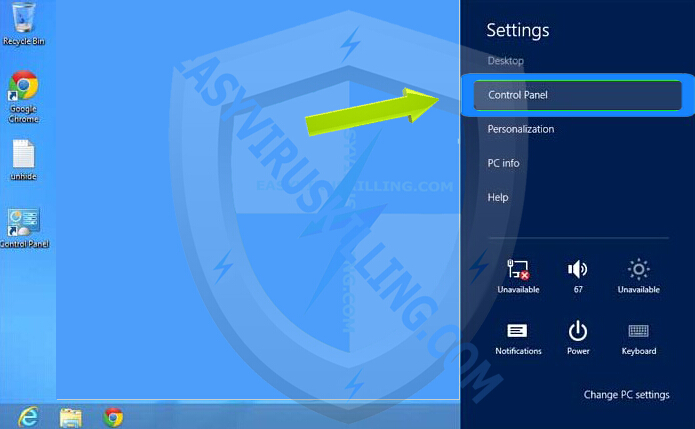
2. In category view, click on Uninstall a program under the Programs category

3. In the Programs and Features window, click Installed On to display the latest programs, scroll through the list to seek and uninstall Tphwabi Extension and other unwanted and unfamiliar programs that look suspicious.

Step Five. Delete unwanted and unknown IE plug-in, Firefox add-on and Chrome extensions related with tphwabi Extension
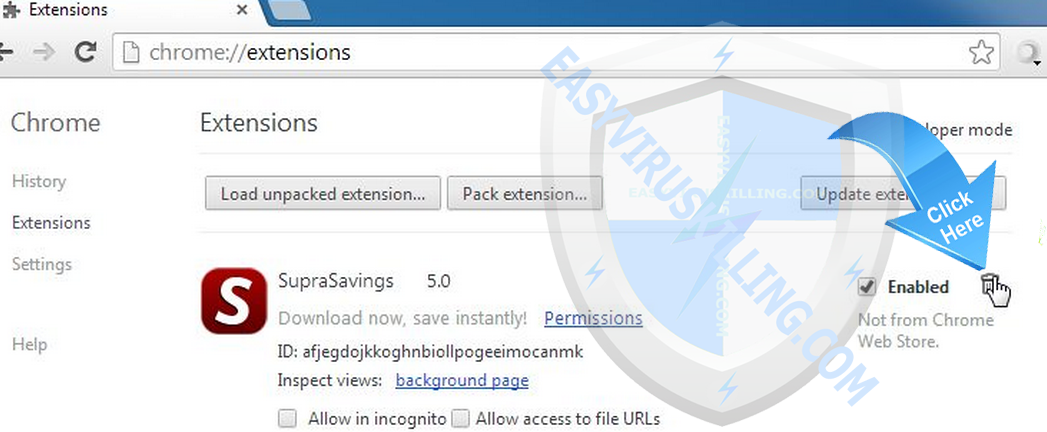
On Chrome
- Click the Chrome menu
 on the browser toolbar.
on the browser toolbar. - Click Tools.
- Select Extensions.
- Click the trash can icon
 to delete tphwabi Extension extension.
to delete tphwabi Extension extension. - Make sure to remove all extensions you do not know or need.
- A confirmation dialog appears, click Remove.
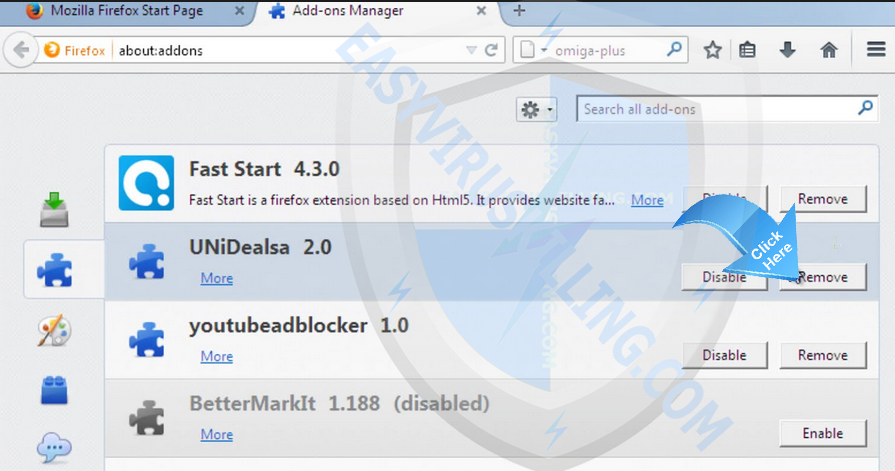
On Firefox
- Click the menu button

 and choose Add-ons. The Add-ons Manager tab will open.
and choose Add-ons. The Add-ons Manager tab will open. - In the Add-ons Manager tab, select the Extensions panel.
- Make sure to remove all extensions you do not know or need.
- Click Disable or Remove button of tphwabi Extension.
- Click Restart now if it pops up.
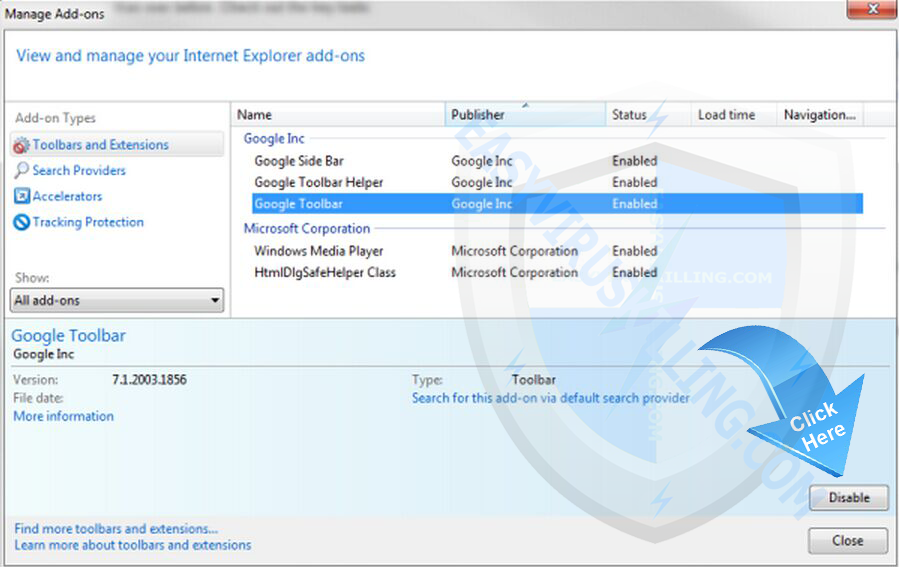
On Internet Explorer
- Open the IE, click the Tools button

, and then click Manage add-ons.
- Click Toolbars and Extensions on left side of the window., and then select tphwabi Extension
- Make sure to remove all BHO’s you do not know or need.
- If the add-on can be deleted, you’ll see the Remove option. Click Remove and then click Close. Otherwise click Disable button.
Automatic Steps (Good and easy for most of PC users to delete tphwabi Extension )
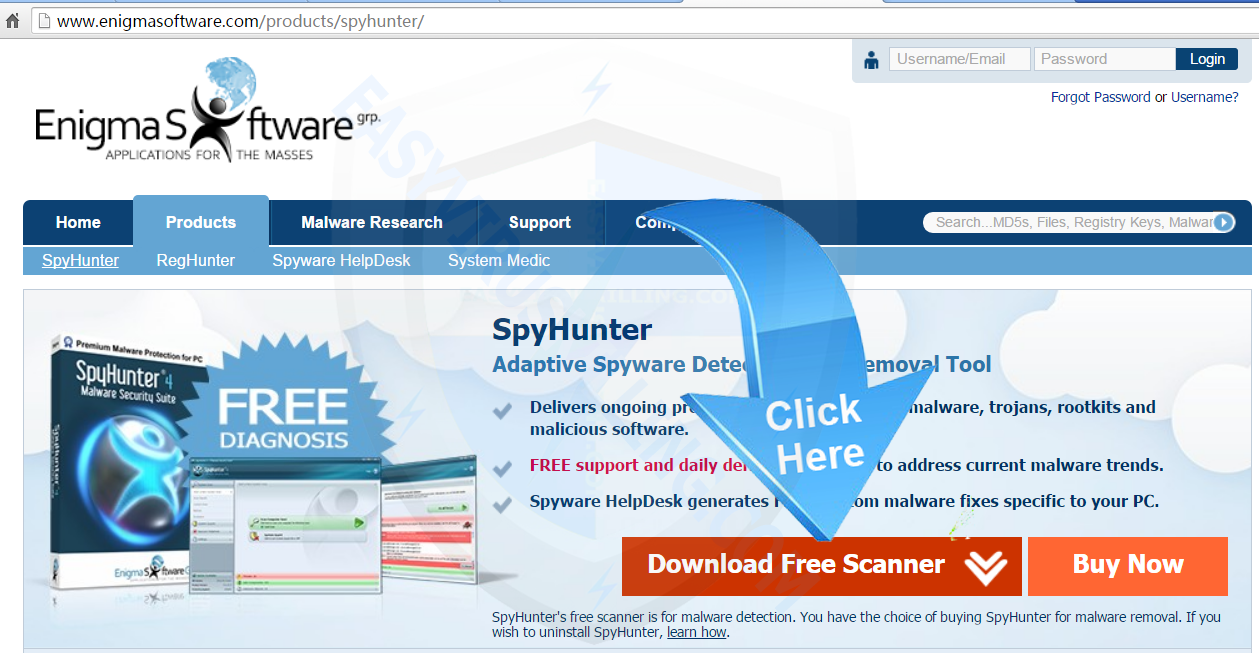
Step One. Install SpyHunter to remove tphwabi Extension virus and other hidden threats.
1. Click the blue button below to open of SpyHunter.
(Notes – SpyHunter’s free version can only help you detect malware or virus. If you want to remove the malware threats detected by SpyHunter, you will need to buy license of SpyHunter. If you do not need it any more, please follow instructions on SpyHunter uninstall)
2. On the page, please click Download Free Scanner to download SpyHunter safely and quickly.
Tips: After SpyHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning ” This type of file can harm your computer. Do you want to keep Download_Spyhunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, please double-click SpyHunter-Installer.exe to start the installation of SpyHunter.
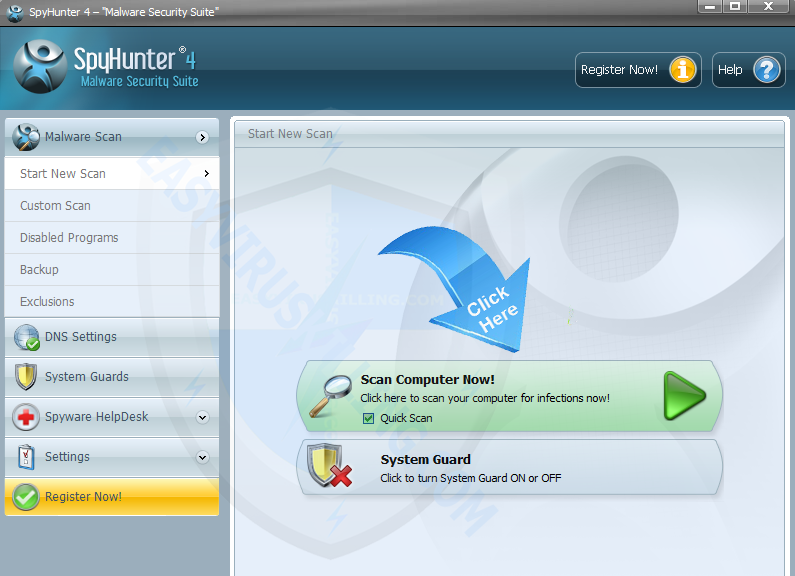
4. When SpyHunter is installed, it will be run automatically, then click Scan Computer Now to detect tphwabi Extension related threats:
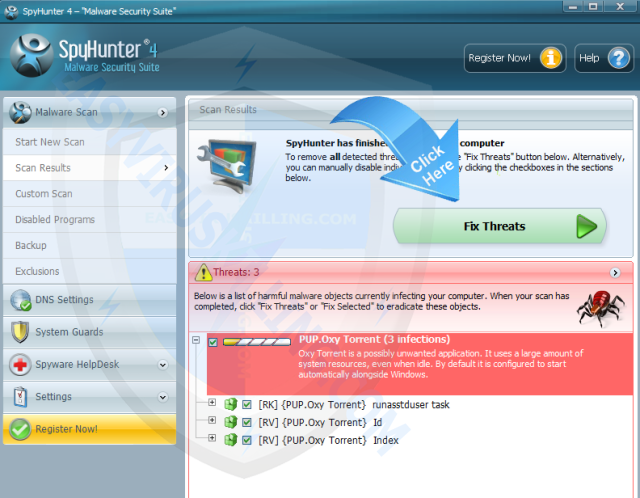
5. Once SpyHunter completes the scan, please click Fix Threats to get rid of tphwabi Extension.
Step Two. Install RegHunter to fix all damaged registry files and make up the security exploits.
1. Click the green button below to open of RegHunter:
(Notes – RegHunter’s free version can only help you scan Registry errors or system errors. If you want to fix the errors detected by RegHunter, you will need to buy license of RegHunter. If you do not need it any more, please follow instructions on RegHunter uninstall)
2. On the page, please click Free PC Diagnosis to download RegHunter safely and quickly.
Tips: After RegHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning “This type of file can harm your computer. Do you want to keep Download_Reghunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, then double-click RegHunter-Installer.exe to start the installation of RegHunter.
4. When RegHunter is installed, it will be run automatically, then click Scan for Registry Errors Now! to detect files corrupted by tphwabi Extension:

5. Once RegHunter completes the scan, please click Repair All Errors to solve security bugs related with tphwabi Extension.
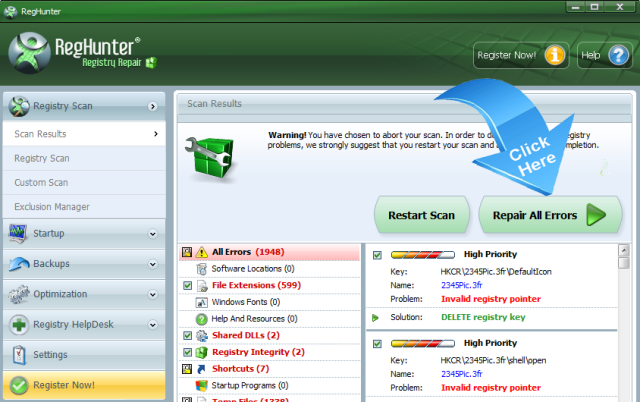
Step Three. Reset Chrome, Firefox and IE to clean up all malicious codes and cookies of tphwabi Extension.
– Reset Chrome
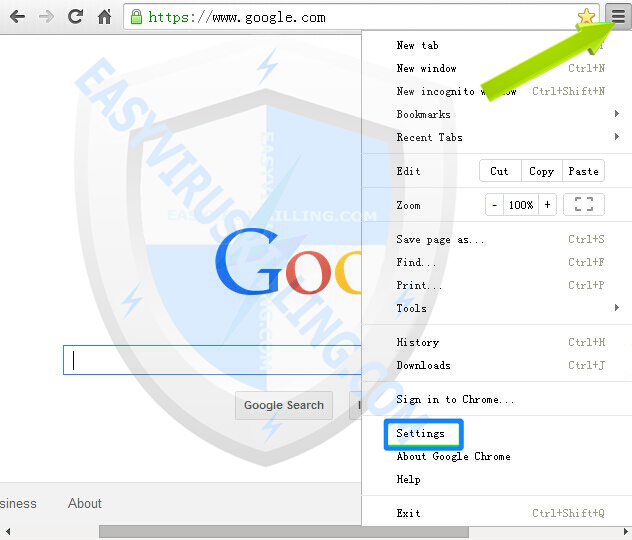
1. Open Chrome, then click “Customize and control Google Chrome” button, and then click on Settings
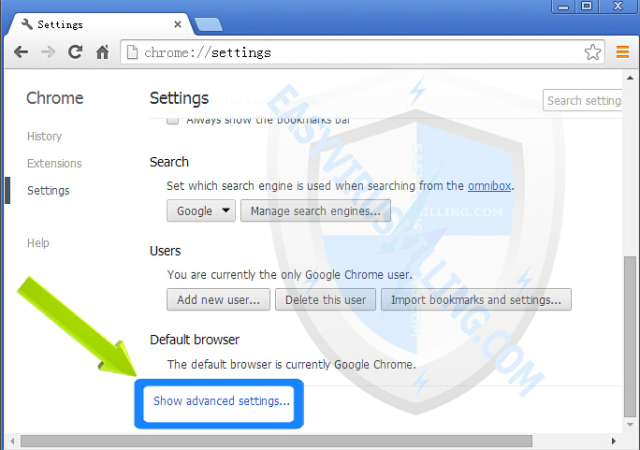
2. Under the Chrome Settings page, scroll down to the bottom, then click on Show advanced settings button
3. After clicking on Show advanced settings button, scroll down to the bottom and click on Reset browser settings button
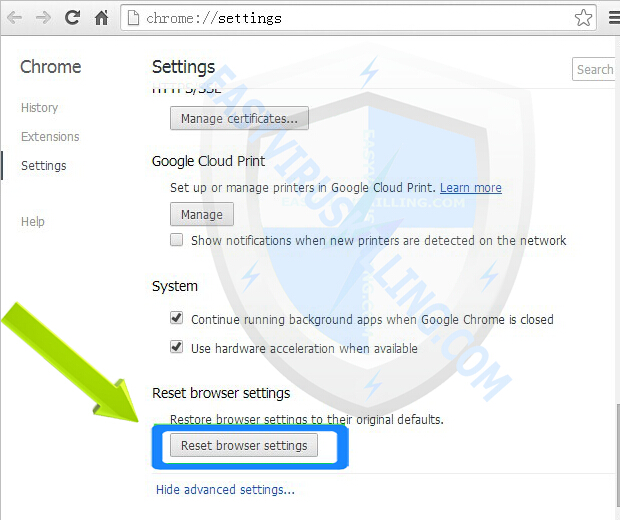
4. A message box will pop up to inform that your browser settings will be restored to their original defaults, click Reset button when it appears:
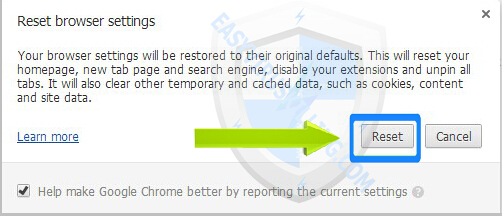
————————————————————————————————————————————————————————————————————–
– Reset Firefox
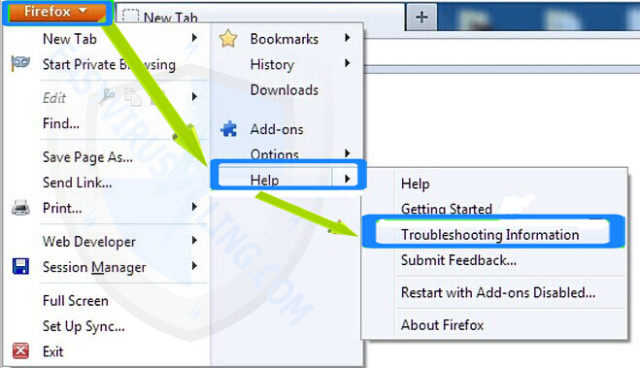
1. Open Firefox, then click on Firefox button, then Click on Help button, then Click on Troubleshooting Information
2. At the Troubleshooting Information page, click on Reset Firefox
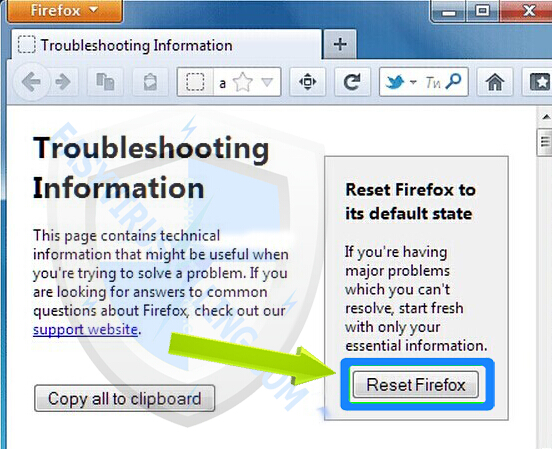
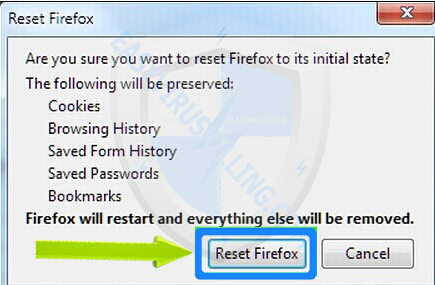
3. A message box will pop up to let you confirm that you want to reset Firefox to its initial state, click Reset Firefox button when it appears:
————————————————————————————————————————————————————————————————————–
– Reset Internet Explorer
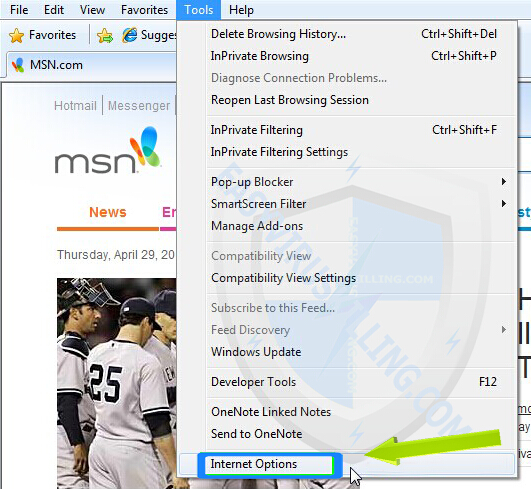
1. Open Internet Explorer, then click on Tools, then click on Internet Options
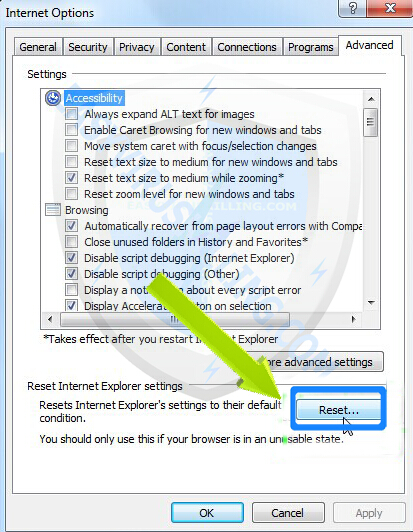
2. On the Internet Options window: click on Advanced tab, then click Reset button
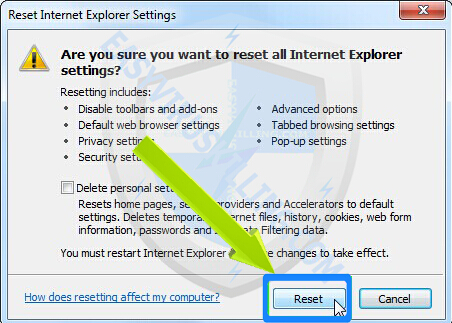
3. A message box will pop up to let you confirm that you want to reset all Internet Explorer Settings, click Reset button when it appears:
4. When the resetting process is done, you’ll see this message box, click Close
5. You’ll need to restart your Internet Explorer to complete the resetting process.
If you have done each step above accurately, you can get rid of tphwabi Extension virus completely. Hope you can solve the issue and get your healthy computer back. Good luck 🙂





