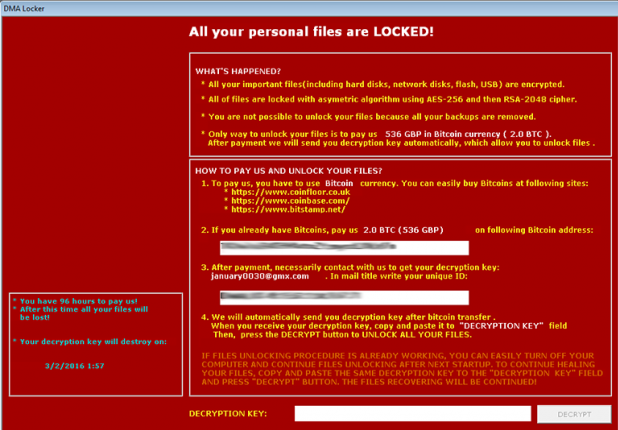
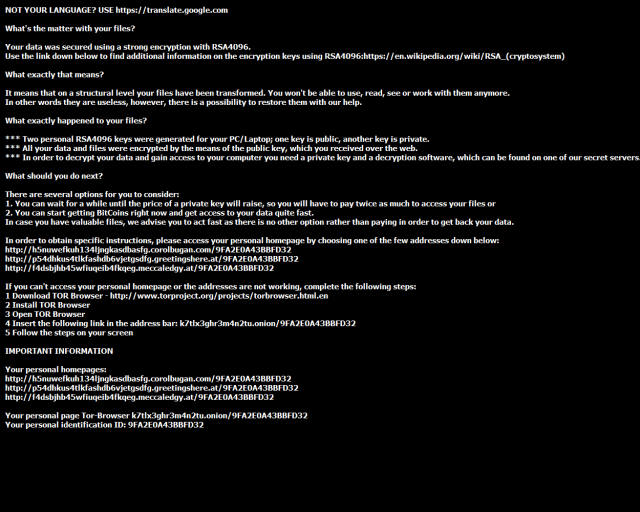
What is Ransom:Win32/Teerac.B!bit?
Ransom:Win32/Teerac.B!bit is deemed as data locking ransomware. It gets in the PC for looting money from users. Just after it comes in, your PC is unavoidably controlled by it. The system, as well as the records and documents will be in threat. It will drag down the system operation and bring about the blue screen of death on the PC. Along these lines, we trust that you ought to remove it as soon as possible.
Ransom:Win32/Teerac.B!bit is acquired by spam email
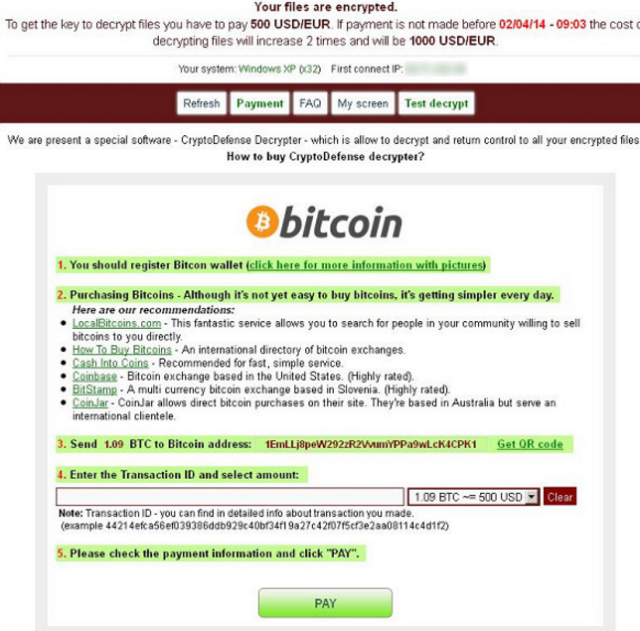
These days, users will get their bill of credit card by email. Indeed, even some of them who have no Visa will take it real when they get messages from bank. So the makers of Ransom:Win32/Teerac.B!bit take advantage of such psych and send them messages with subjects identified with this bank. So when these messages are opened, Ransom:Win32/Teerac.B!bit gets itself introduced on your PC. Continue reading