Exploit.Win32.CVE-2010-2568.gen Instruction
Exploit.Win32.CVE-2010-2568.gen is a nasty pest usually sneaks into your computer secretly when you visit malicious contents or download free items from infected websites unwarily. Once Exploit.Win32.CVE-2010-2568.gen infiltrates your system, it will alter the registry to make itself a startup task, which means that it can be activated when your PC starts. Once activated, it will execute malicious codes to generate many suspicious processes in the background, which not only will occupy the great mass of your system resource, but also execute harmful tasks to mess up the whole system. Furthermore, it generates backdoor to connect the remote server to download various high-risk malware which may modify your system settings, registry settings, browser settings or even disables your Windows Task Manager and other normal program functions. What’s worse, this nasty Trojan may give a pathway for the cyber criminal to get access to your computer or even take the full control of it. After that, the cyber criminal will take the chance to attack the weak administrator passwords and steal your personal information without your awareness which may make you suffer from money loss. Now it is high time for you to take steps to remove the Trojan horse from your computer, so as to avoid other damages to your system and protect your precious data.
Other System Corruptions Caused by Exploit.Win32.CVE-2010-2568.gen
1. System operation become very slowly, and you can see high CPU usage (i.e. 90% CPU usage) in Task Manager even when you just launches your system.
2. Documents and files suddenly disappear (removed by the virus); some folders cannot be opened;
3. Lots of ads pop-ups are bombarding you o rand your browser meets re-directs problems;
4. Some of your programs start to become invalid; and some unknown programs are installed silently;
5. You get more and more system crash and random BSOD; it takes excessively long time to get into Windows; etc.
Exploit.Win32.CVE-2010-2568.gen Quick Removal Tool
SpyHunter is a top-class antispyware / antimalware program which can help you detect an remove viruses and malware like Trojan Horse, Rootkits, Worms, Browser Hijacker, Adware, Pop-ups, Spyware, Rogue Programs and more. It is designed with industry-leading innovative technologies which help defend your PC against all infections attacking. It detects and protects against malware in real-time, blocks hacking and phishing attempts, schedules automatic scanning to keep your PC secure, healthy and fast. There are over 80 million PC users securing their system with SpyHunter. SpyHunter is designed to work alongside existing security programs, thus it will not cause any conflict with your installed security programs or slow down your computer running. Follow the quick steps below to remove Exploit.Win32.CVE-2010-2568.gen quickly and easily.
Solutions for Exploit.Win32.CVE-2010-2568.gen Virus Removal (Remove Exploit.Win32.CVE-2010-2568.gen Step-by-Step)
Here are 3 different solutions to remove Exploit.Win32.CVE-2010-2568.gen virus. Solution A is the most complicated way that only advanced users can handle, if you are not so great on your PC skills and experienced in handling virus manually, do not use this solution, or you may cause severe problems. We recommend most of PC users to directly try Solution B and Solutions C , which are easy and effective for removing masses of computer threats such as Exploit.Win32.CVE-2010-2568.gen.
Solution A (Complicated Manual Removal method – only for Advanced and Experienced PC users with top skills)
Step 1. Change system folder settings to show all hidden files
Step 2. Seek and delete Exploit.Win32.CVE-2010-2568.gen related files in hidden folders
Step 3. Seek and remove Exploit.Win32.CVE-2010-2568.gen related registry files
Solution B (Best, easiest and most-used method)
Step 1. Uninstall Exploit.Win32.CVE-2010-2568.gen related programs from your computer
Step 2. Remove Exploit.Win32.CVE-2010-2568.gen plug-in, toolbar, add-on, extension from IE/Firefox/Chrome
Step 3. Scan your computer with SpyHunter to remove Exploit.Win32.CVE-2010-2568.gen infection (Important Step)
Solution C (Effective method for removing stubborn malware )
Step 1. Run RegHunter to detect security bugs and fix corrupted/modified system files used by Exploit.Win32.CVE-2010-2568.gen for re-infiltration (Important Step)
Step 2. Reset Chrome, Firefox and IE to remove Exploit.Win32.CVE-2010-2568.gen
Solution A – Exploit.Win32.CVE-2010-2568.gen Manual Removal
Step 1. Change system folder settings to show all hidden files
On Windows 7 / Vista Computer
- Right-click the Windows Logo button and choose Open Windows Explorer.
- Click Organize and choose Folder and Search Options.
- Click the View tab, select Show hidden files and folders and then clear the checkbox for Hide protected system operating files.
- Click Yes on the warning and then click OK.
On Windows 8 Computer
- On your keyboard press the Windows + E keys.
- Click the View tab.
- Check File name extensions and Hidden items
Step 2. Seek and delete Exploit.Win32.CVE-2010-2568.gen related files in hidden folders listed below:
(The files on your computer may appear with different name, if cannot find out the files listed below, do not delete any file, just use Solution B and Solution C)
%Temp%\[adware name]
%AppData%\[adware name]
%LocalAppData%\[adware name]
%LocalAppData%\[adware name].exe
%CommonAppData%\[adware name]
%AllUsersProfile%random.exe
Step 3. Seek and remove Exploit.Win32.CVE-2010-2568.gen related registry files listed below:
1. Open Registry Editor first:
On Windows 7 / Vista Computer
- Click Start button
- Select Run button
- Type: regedit
- Click OK button
On Windows 8 Computer
- Press Win [Windows key] + R on your keyboard. This can be done either while at Windows 8 Start menu/Metro screen or on Windows 8 desktop
- At the dialog box that pops open, type regedit.exe and hit OK
- Once you hit OK, Windows UAC will prompt you to confirm you want to open Register Editor — hit “Yes”
2. Find out and remove all harmful registry files related with Exploit.Win32.CVE-2010-2568.gen virus listed below:
(The registry files on your computer may appear with different name, if cannot find out the files listed below, do not delete any file, just use Solution B and Solution C)
HKEY_LOCAL_MACHINESOFTWAREsupWPM
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesWpm
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain “Default_Page_URL”
HKEY_LOCAL_Machine\Software\Classes\[adware name]
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\[adware name]
Notes: Manual removal needs advanced PC skills, if you cannot find the Exploit.Win32.CVE-2010-2568.gen files accurately, you may ruin your system for removing important system files. Therefore, if you are not a user with Advanced tech skills, it’s best to use Solution B or Solution C to solve your problem easily and safely.
Solution B – Exploit.Win32.CVE-2010-2568.gen Easy Removal Method
Step 1. Uninstall Exploit.Win32.CVE-2010-2568.gen related programs from your computer
On Windows 7 / Vista Computer
1. Click on the Start button to open your Start Menu, then Click Control Panel
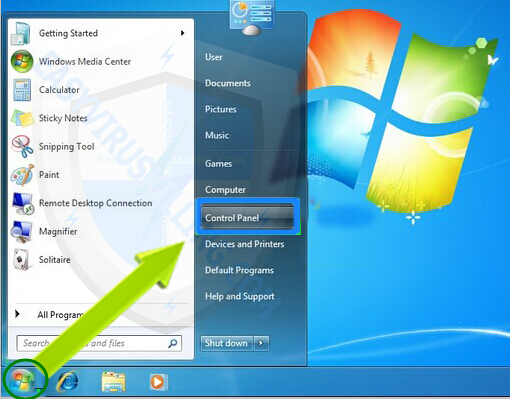
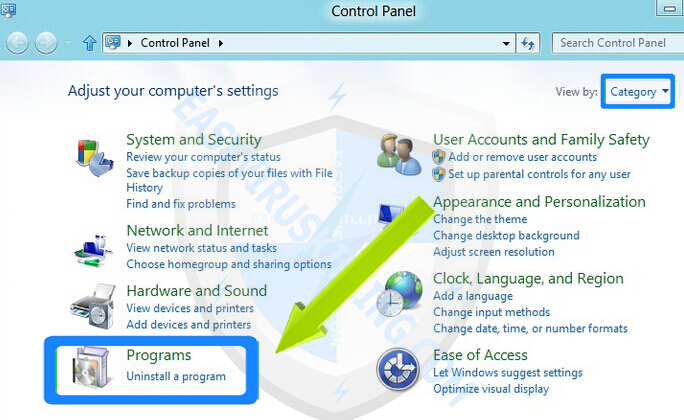
2. In Control Panel, click on Uninstall a program under the Programs category
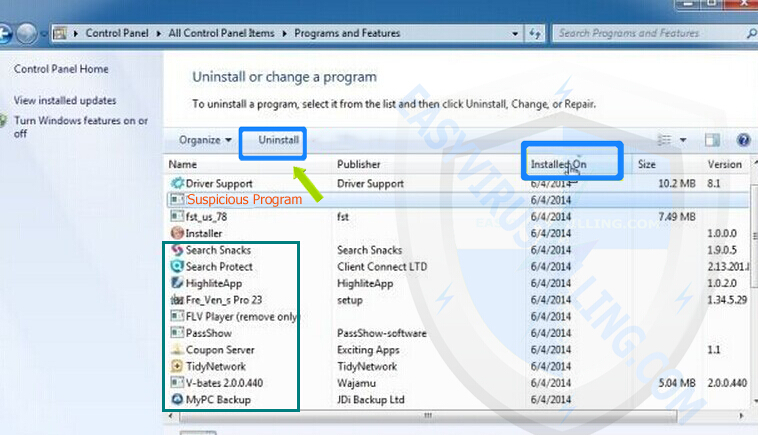
3. In the Programs and Features window, click Installed On to display the latest programs, scroll through the list to seek and uninstall Exploit.Win32.CVE-2010-2568.gen and other unwanted and unfamiliar programs that look suspicious.
On Windows 8 Computer
1. Open the Settings Charm Bar by pressing Windows key  + I key on your keyboard at the same time, then click on the Control Panel option
+ I key on your keyboard at the same time, then click on the Control Panel option
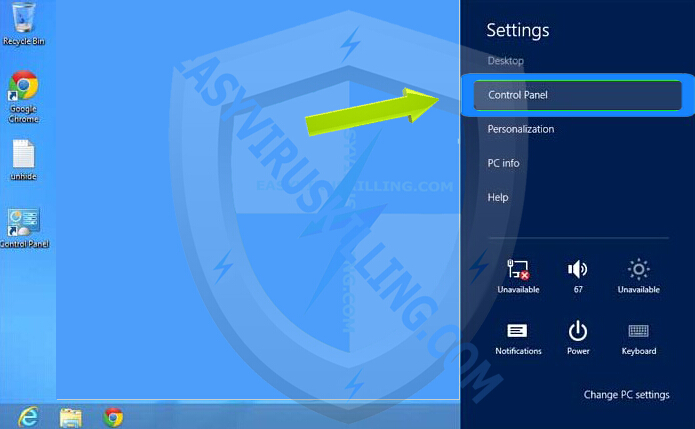
2. In category view, click on Uninstall a program under the Programs category

3. In the Programs and Features window, click Installed On to display the latest programs, scroll through the list to seek and uninstall Exploit.Win32.CVE-2010-2568.gen and other unwanted and unfamiliar programs that look suspicious.

Step 2. Remove Exploit.Win32.CVE-2010-2568.gen plug-in, toolbar, add-on, extension from Chrome/Firefox/IE
On Chrome
- Click the Chrome menu
 on the browser toolbar.
on the browser toolbar. - Click Tools.
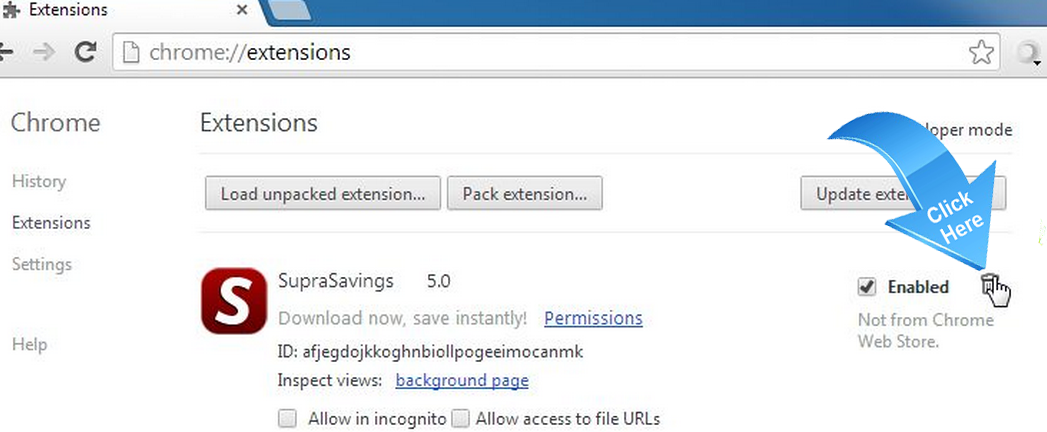
- Select Extensions.
- Click the trash can icon
 to delete Exploit.Win32.CVE-2010-2568.gen extension.
to delete Exploit.Win32.CVE-2010-2568.gen extension. - Make sure to remove all extensions you do not know or need.
- A confirmation dialog appears, click Remove.
On Firefox
- Click the menu button

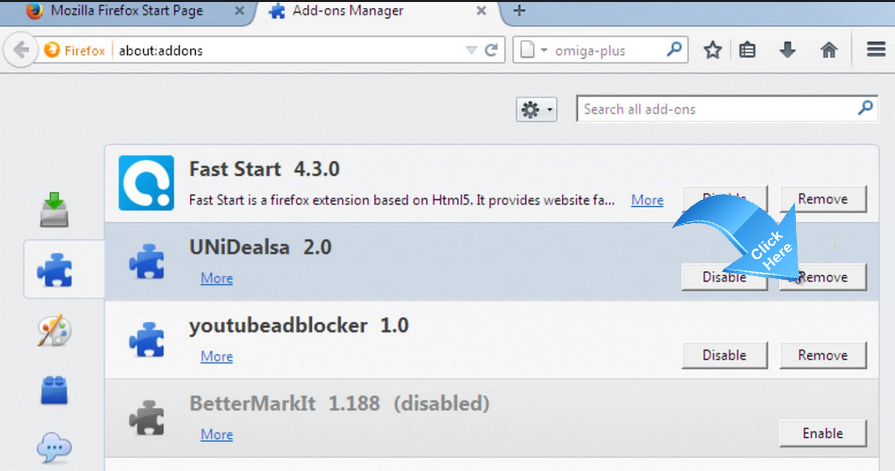
 and choose Add-ons. The Add-ons Manager tab will open.
and choose Add-ons. The Add-ons Manager tab will open. - In the Add-ons Manager tab, select the Extensions panel.
- Make sure to remove all extensions you do not know or need.
- Click Disable or Remove button of Exploit.Win32.CVE-2010-2568.gen.
- Click Restart now if it pops up.
On Internet Explorer
- Open the IE, click the Tools button

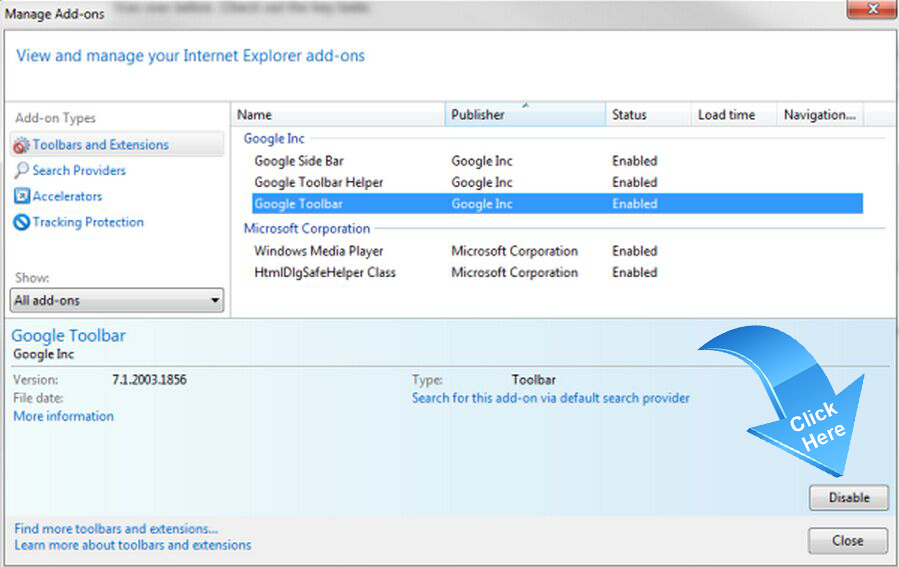
, and then click Manage add-ons.
- Click Toolbars and Extensions on left side of the window., and then select Exploit.Win32.CVE-2010-2568.gen
- Make sure to remove all BHO’s you do not know or need.
- If the add-on can be deleted, you’ll see the Remove option. Click Remove and then click Close. Otherwise click Disable button.
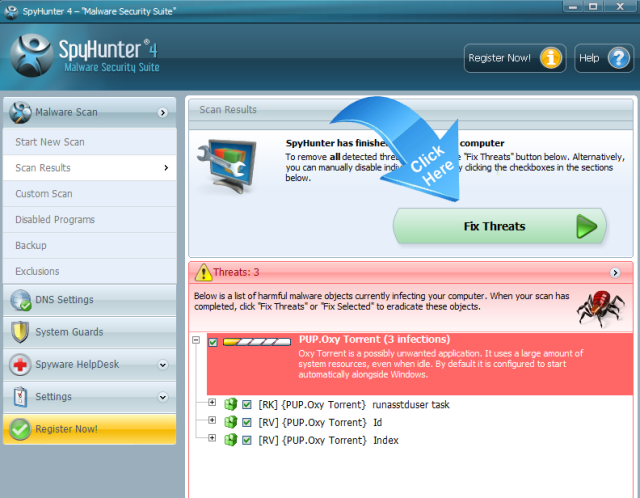
Step 3. Scan your computer with SpyHunter to remove Exploit.Win32.CVE-2010-2568.gen infection (Important Step)
Uninstallation of program in Control Panel and removal of extensions / add-on from web browsers can help us remove parts of adware and malware, but nowadays most of computer threats such as Exploit.Win32.CVE-2010-2568.gen are created with advanced technology and cannot be easily removed with regular methods, therefore we need to use top-class malware remover like SpyHunter to get rid of threats automatically. To completely remove Exploit.Win32.CVE-2010-2568.gen, you should download and run SpyHunter antimalware to diagnose your computer and get rid of all threats related with the virus.
1. Click the blue button below to open of SpyHunter.
(Notes – SpyHunter’s free version can only help you detect malware or virus. If you want to remove the malware threats detected by SpyHunter, you will need to buy license of SpyHunter. If you do not need it any more, please follow instructions on SpyHunter uninstall)
2. On the page, please click Download Free Scanner to download SpyHunter safely and quickly.
Tips: After SpyHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning ” This type of file can harm your computer. Do you want to keep Download_Spyhunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, please double-click SpyHunter-Installer.exe to start the installation of SpyHunter.

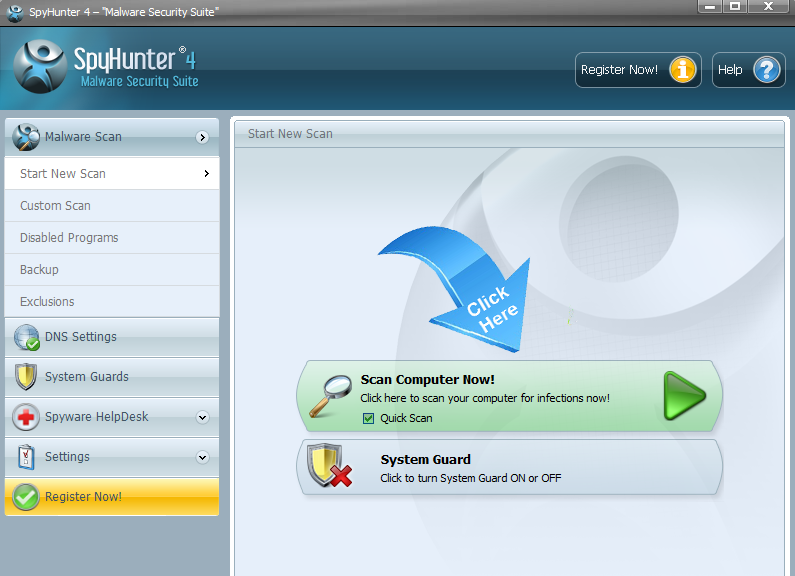
4. When SpyHunter is installed, it will be run automatically, then click Scan Computer Now to detect Exploit.Win32.CVE-2010-2568.gen related threats:
5. Once SpyHunter completes the scan, please click Fix Threats to get rid of Exploit.Win32.CVE-2010-2568.gen.
Note: According to users investigation, this solution can help 95% users remove virus like Exploit.Win32.CVE-2010-2568.gen completely. But if it does not function on your computer, you need to complete all steps listed in Solution C. Continue now:
Solution C – Exploit.Win32.CVE-2010-2568.gen Quick Removal Guideline
Step 1. Run RegHunter to detect security bugs and fix corrupted/modified system files used by Exploit.Win32.CVE-2010-2568.gen for re-infiltration (Important Step)
If you tried Solution B and still unable to remove Exploit.Win32.CVE-2010-2568.gen, then we are sure that some of your system files must been modified or damaged by the virus. With a deep investigation and test on stubborn malware such as Exploit.Win32.CVE-2010-2568.gen, our tech team confirm that the security bugs and system files modified /corrupted by virus is the reason why the threats survive and reborn.
Most of spyware and malware infect Windows machines by making use of existed security bugs, and they alter or corrupt crucial system files with codes, that means malware like Exploit.Win32.CVE-2010-2568.gen is able to execute installation or activation codes of its program repeatedly, no matter how many times you delete it from Control Panel or extensions. Therefore, if you do not detect and fix all security bugs and restore the corrupted / modified system files to default, Exploit.Win32.CVE-2010-2568.gen can keep coming back. In such situation, it’s best to run RegHunter to fix security bugs and corrupted files, hindering the reborn and re-infiltration of Exploit.Win32.CVE-2010-2568.gen.
1. Click the green button below to open of RegHunter:
(Notes – RegHunter’s free version can only help you scan Registry errors or system errors. If you want to fix the errors detected by RegHunter, you will need to buy license of RegHunter. If you do not need it any more, please follow instructions on RegHunter uninstall)
2. On the page, please click Free PC Diagnosis to download RegHunter safely and quickly.
Tips: After RegHunter is downloaded, your Chrome /Firefox /IE may display such fake security warning “This type of file can harm your computer. Do you want to keep Download_Reghunter-Installer.exe anyway?”, which is generated by virus to cheat you, please just ignore the fake warning and click “Keep” button.
3. Once downloaded, then double-click RegHunter-Installer.exe to start the installation of RegHunter.
4. When RegHunter is installed, it will be run automatically, then click Scan for Registry Errors Now! to detect files corrupted by Exploit.Win32.CVE-2010-2568.gen:

5. Once RegHunter completes the scan, please click Repair All Errors to solve security bugs related with Exploit.Win32.CVE-2010-2568.gen.
Step 2. Reset Chrome, Firefox and IE to remove Exploit.Win32.CVE-2010-2568.gen
– Reset Chrome
1. Open Chrome, then click “Customize and control Google Chrome” button, and then click on Settings
2. Under the Chrome Settings page, scroll down to the bottom, then click on Show advanced settings button
3. After clicking on Show advanced settings button, scroll down to the bottom and click on Reset browser settings button
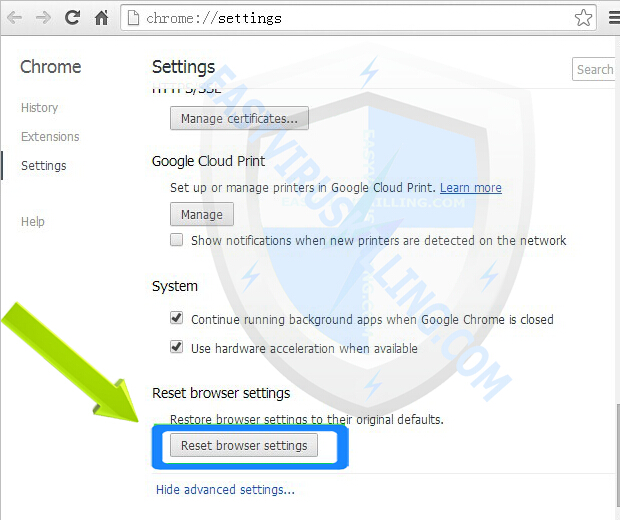
4. A message box will pop up to inform that your browser settings will be restored to their original defaults, click Reset button when it appears:
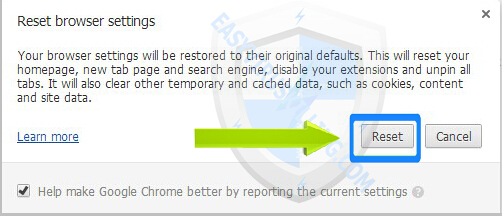
————————————————————————————————————————————————————————————————————–
– Reset Firefox
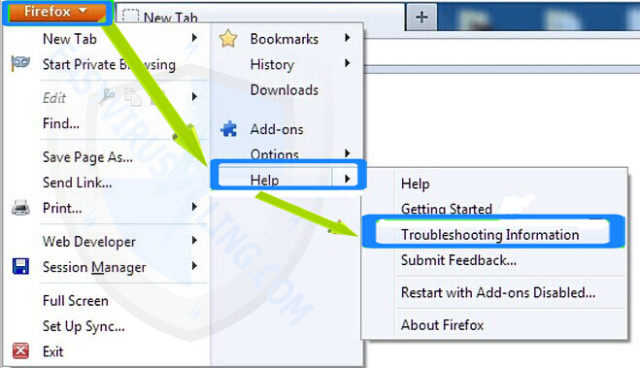
1. Open Firefox, then click on Firefox button, then Click on Help button, then Click on Troubleshooting Information
2. At the Troubleshooting Information page, click on Reset Firefox
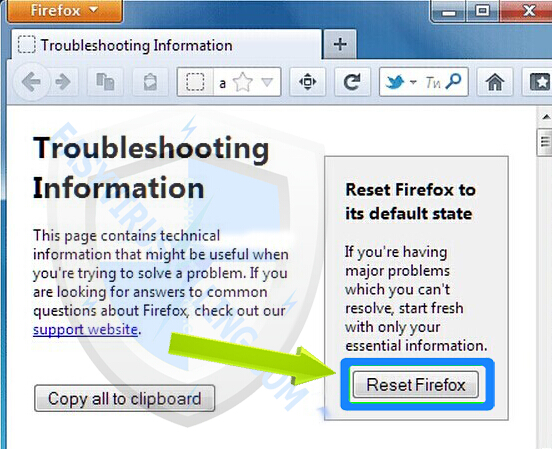
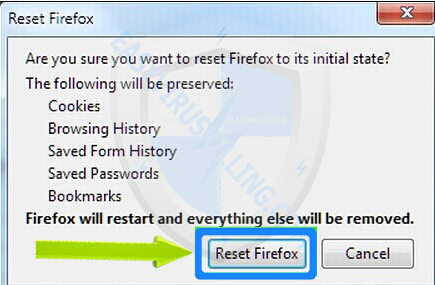
3. A message box will pop up to let you confirm that you want to reset Firefox to its initial state, click Reset Firefox button when it appears:
————————————————————————————————————————————————————————————————————–
– Reset Internet Explorer
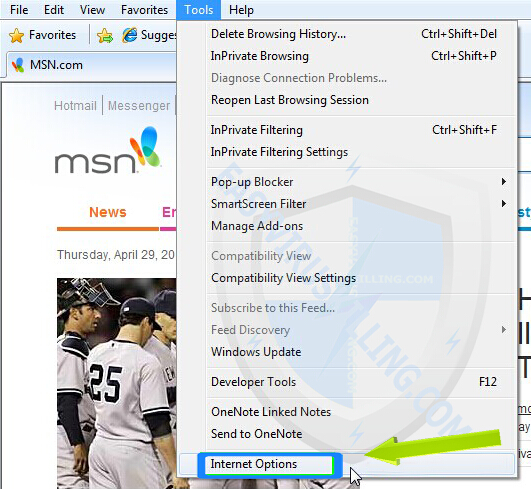
1. Open Internet Explorer, then click on Tools, then click on Internet Options
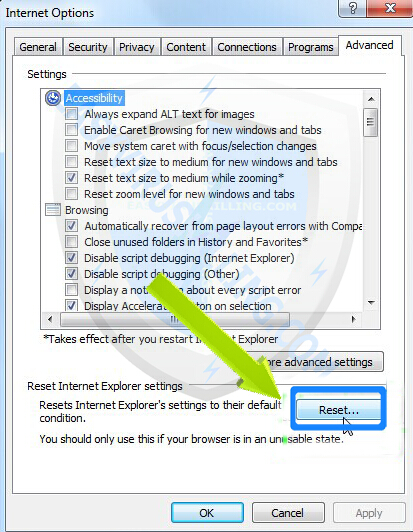
2. On the Internet Options window: click on Advanced tab, then click Reset button
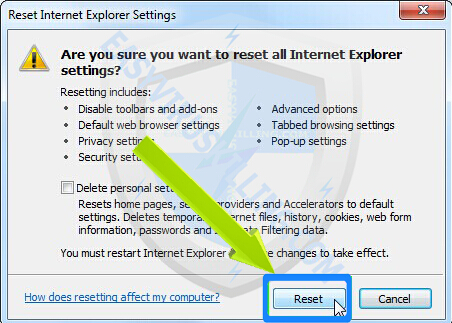
3. A message box will pop up to let you confirm that you want to reset all Internet Explorer Settings, click Reset button when it appears:
4. When the resetting process is done, you’ll see this message box, click Close
5. You’ll need to restart your Internet Explorer to complete the resetting process.
After completing the three solutions, your computer should be safe and healthy now. Just take a few more minutes to read the important tips on how to protect your computer and avoid virus infections. It’s worth to read. Catch it now:
How to Protect Your PC from Viruses & Malware (Important Tips)
1. Install a top-class Antivirus to keep you safe online.
Currently, 98% computer viruses and malware are spread via Internet. To keep your PC secure and healthy, the most important thing is to install really effective and efficient antivirus software capable of keeping you safe online. New computer threats are created every second and they are more and more stubborn and tricky. It’s not an easy thing for PC users to select the best antivirus that can prevent Malware, Adware, Spyware, Trojan Horse,Phishing, Ransomware , Unsecure Shopping and Identity Theft. Therefore our tech team tested and reviewed over 100 antivirus programs, finally we pick out the best of the best antivirus software to help you make the smart choice, including Kaspersky Total Security , Trend Micro, and Bitdenfender. It’s highly recommended to install one of them to provide your computer with overall effective and real-time protection.



2. Pay attention to unknown email
Lots of viruses and malware are attached on emails, when you receive emails from unfamiliar sender or unknown source, it’s best not to open any attachment unless it’s something you’re expecting. Besides, cyber criminal often use emails to execute their scam activities, pay attention to those unknown emails titled with keywords related Free things or prize, and do not click any link in such spam emails.
3. Always turn on User Account Control (UAC)
On Windows systems above Windows XP, the User Account Control is another effective function to hinder virus activities. UAC always notifies you and ask you to permit the change when changes are going to be made to your PC that require administrator-level permission. It is strongly suggested to keep the UAC active, since it can prevent malicious changed performed by virus and malware.
4. Always choose “custom install ” when installing free programs
Free programs now have become one of the major channels spreading Potentially Unwanted Programs (PUP), Adware, Spyware and Browser Hijacker. Usually, when you download and install free programs on third party websites, some threats like Exploit.Win32.CVE-2010-2568.gen is installed without your knowledge if you select the “typical install”. To protect your PC from unwanted and harmful programs, it’s best to choose “custom install ” when you install free programs, and you should Uncheck all the boxes which prompt you to install bundled programs.